Cyber incidents are skyrocketing in 2026, with startups being the primary targets. Limited budgets, lean teams, and a focus on growth over security make emerging businesses particularly vulnerable.
Today’s threats go beyond phishing and weak passwords; AI-powered cyberattacks, ransomware-as-a-service (RaaS), and deepfake scams are hitting startups harder than ever. To protect sensitive data and customer trust, startups must adopt smarter, AI-driven cybersecurity strategies without breaking the bank.
Here are practical, cost-effective, and AI-backed ways to secure your startup in 2026.
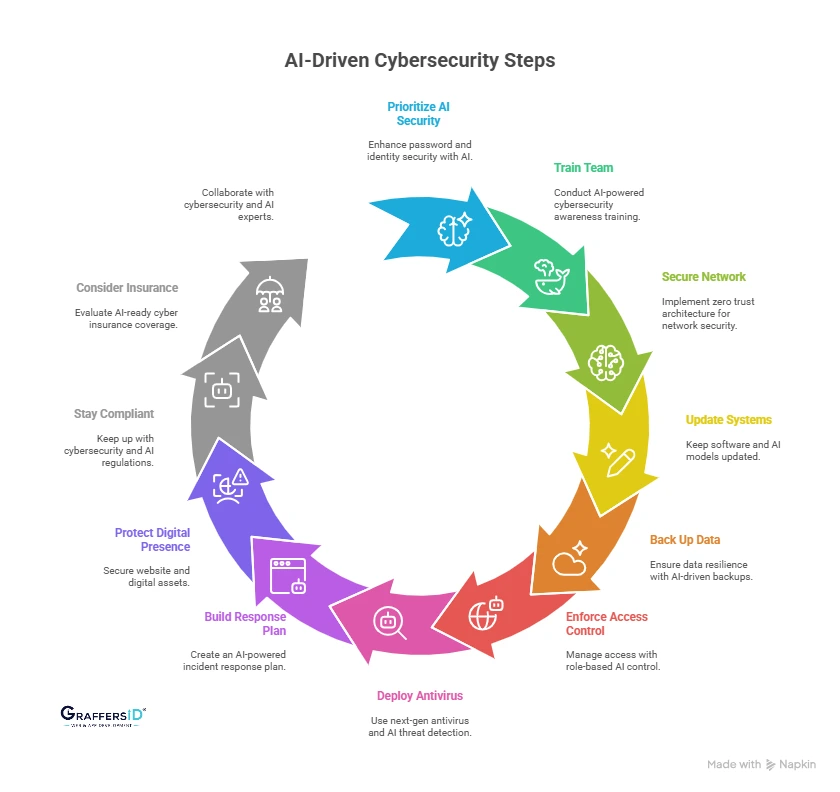
1. Prioritize AI-Enhanced Password & Identity Security
The use of weak passwords is one of the greatest delinquencies any organization can have. Make sure your team adheres to the proper password every time:
-
Adopt passwordless authentication (biometric logins, passkeys).
-
Use AI-powered password managers like 1Password or Dashlane with real-time breach detection.
-
Enable MFA/2FA across apps, ideally with adaptive AI that detects unusual login behavior.
-
Rotate credentials automatically using enterprise tools to reduce manual overhead.
💡 Pro Tip: Use AI-driven identity and access management (IAM) solutions to detect unusual login attempts, preventing credential stuffing attacks.
2. Train Your Team with AI-Powered Cybersecurity Awareness
Employees are the first line of defense, but attackers now use AI to create phishing emails indistinguishable from real ones.
- Continuous training with AI simulators that mimic real phishing attempts.
- Gamified learning to keep employees engaged.
- Dark web exposure alerts: Train staff to recognize warning signs if credentials are leaked.
3. Secure Your Network with Zero Trust Architecture
When a network is breached, there could be grave repercussions. Therefore, protecting your network is very important, especially for your new company. Traditional firewalls are no longer enough. Zero Trust is the 2026 standard.
-
Implement Zero Trust access: “Never trust, always verify.”
-
AI-driven VPN alternatives (ZTNA) for secure remote access.
-
Automated traffic monitoring using AI anomaly detection.
-
Microsegmentation to isolate breaches and limit lateral movement.
Read Also: Data Privacy in the Digital Age
4. Keep Software & AI Models Updated
As noted, the earlier-mentioned attacks are usually initiated from the network’s marked gateways. Attackers now exploit outdated AI models and APIs.
- Enable auto-updates: This ensures that all OS, SaaS, and AI integrations are up-to-date.
- Retire outdated tools: The software that has become outdated can bring serious threats, so make sure to remove it, especially unused cloud services.
- Use AI patch management tools: Be sure to keep up with the software threats, identify vulnerabilities faster, and fix them as soon as they come.
5. Back Up Data with AI-Driven Resilience
Data is the lifeblood of startups, and ransomware attacks are on the rise. It is always distressing to lose data, but it is better to know that there are backups to help in such situations.
- Follow the 3-2-1-1 rule: Have a minimum of three copies of the data, have 2 formats of them on different media, and have one of them in immutable storage.
- AI-monitored backups: Ensure that, every so often, the information that is backed up is both intact and accessible.
- Cloud-native storage: Most reputable cloud service providers, such as AWS, Azure, and Google Cloud, have built-in AI threat detection.
6. Enforce Role-Based AI Access Control
Not every employee needs access to everything. In 2026, access governance is smarter.
-
AI-powered access control (RBAC & ABAC): Implements role-based access control and grants permissions dynamically.
-
Just-in-time (JIT) access: Temporary elevated access instead of permanent rights. Only information needed by the employees in executing their functions should be accessed by them.
-
Audit logs powered by AI: Know who accessed what private information and at what time to flag unusual access attempts.
Read Also: Biggest Cybersecurity Threats And How to Protect Yourself
7. Deploy Next-Gen Antivirus & AI Threat Detection
Classic antivirus isn’t enough in the age of AI malware.
-
Extended Detection & Response (XDR): Combines antivirus, anti-malware, and AI anomaly detection.
-
Behavior-based AI scanning: Detects zero-day malware.
-
Continuous endpoint monitoring via AI-driven tools like CrowdStrike, SentinelOne, or Microsoft Defender AI.
8. Build an AI-Powered Incident Response Plan
Even with prevention, breaches can happen. AI reduces downtime and damage.
-
AI-driven SOAR tools (Security Orchestration, Automation, and Response): Draws up an automated contingency response policy with a description of the actions to be taken when a cyberattack occurs.
-
Run tabletop AI simulations: Rotate duties for incident management following the incident’s response for phishing, ransomware, or insider threats.
-
Define escalation workflows: Assess the execution of your order under various circumstances. with predefined playbooks.
9. Protect Your Website & Digital Presence
Your website is your digital storefront, and hackers know it. For entrepreneurs engaged in business on the internet, protecting a business website is of the essence.
-
Use SSL/TLS with AI monitoring: Create a secure connection between the website and the users.
-
Regular vulnerability scans with AI-based tools like Astra or Detectify.
-
Automated plugin monitoring for outdated CMS extensions.
Read More: AI and Cybersecurity in 2026: Emerging Threats, Global Trends & Cybersecurity Best Practices
10. Stay Ahead of Compliance & AI Regulations
In 2026, data protection is stricter than ever (GDPR, CCPA, Digital India Act, and AI governance laws). Making efforts to obey the laws protecting the information of the people not only helps in avoiding trouble with the law but also enhances the confidence of the people towards your services.
-
Automate compliance reporting with AI-driven GRC (Governance, Risk & Compliance) platforms.
-
Data mapping & classification AI tools to track sensitive customer data.
-
Embed privacy-by-design into product development.
11. Consider Cyber Insurance (AI-Ready Coverage)
With RaaS and AI attacks rising, cyber insurance is a survival tool. Though it might come across as an unnecessary cost, cyber coverage can help your young enterprise avoid incurring considerable expenses.
- Assess policy coverage: Select a plan appropriate for your business requirements. Ensure your policy covers AI-driven threats like deepfake scams.
-
Use insurer-provided AI risk assessment tools: Insurance is a backup plan and cannot replace the need for effective cybersecurity systems.
12. Partner with Cybersecurity & AI Experts
Cybersecurity is evolving too fast for startups to manage alone. You can think about getting assistance from experts.
-
Hire Managed Security Service Providers (MSSPs): These service providers will deliver around-the-clock advanced AI-driven monitoring as well as threat detection.
-
AI security audits & penetration testing from specialists.
-
Outsource IT + security to trusted partners like GraffersID for end-to-end development & compliance.
Conclusion
Cybersecurity in 2026 isn’t optional; it’s existential for startups. With AI-powered threats growing daily, a reactive strategy is no longer enough. By embracing AI-enhanced defense tools, Zero Trust practices, continuous employee training, and expert partnerships, startups can protect customer trust while scaling fearlessly.
At GraffersID, we don’t just build software; we build secure digital ecosystems. From AI development to compliance-first app and web solutions, our in-house developers ensure your startup grows without cyber risks.