In the digital age, our day-to-day lives are increasingly getting connected with technology, and our personal information is constantly being collected by various organizations. This data, including our online activities and shopping preferences, to our health records and financial transactions, is very valuable and vulnerable. Data privacy has become an important concern as we navigate the digital landscape, and it is important to understand how to protect our information from privacy breaches and cyber threats. In this blog, we will discuss what data privacy is, the difference between data protection and data privacy, and best practices for protecting your data and more.
What is Data Privacy?
The proper handling, processing, storing, and use of personal data is referred to as data privacy. This includes everything from your name, email, and location to more sensitive data like financial records and biometric identifiers.
Why Is Data Privacy Important in Today’s World?
Data privacy is of much importance for several reasons:
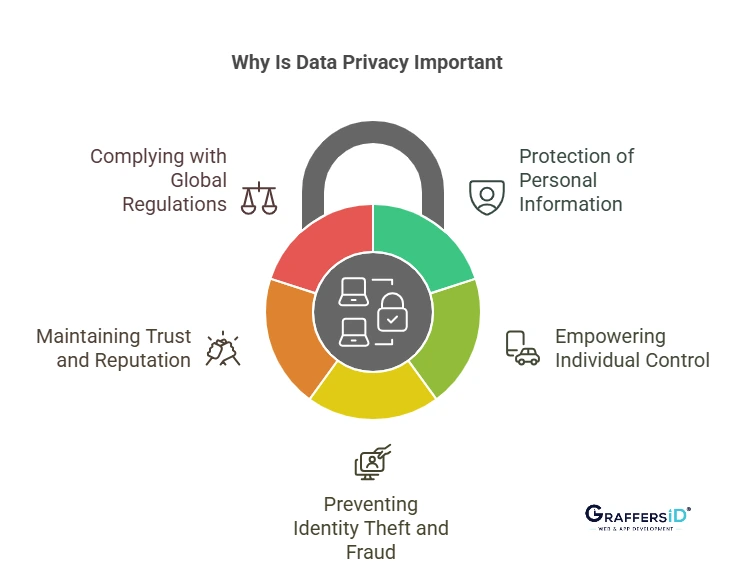
- Protection of Personal Information: Data privacy secures personal details, like financial data, health records, and identity information, from unauthorized access and misuse.
- Empowering Individual Control: Privacy allows individuals to control how their data is collected, used, and shared, giving them control over their digital identities.
- Preventing Identity Theft and Fraud: Without proper security measures, this personal data can be misused by cybercriminals. Weak privacy methods increase the chances of identity theft and fraud.
- Maintaining Trust and Reputation: The reputation of individuals and organizations can be seriously harmed by data breaches. Ensuring privacy helps maintain credibility and trust with clients, customers, and partners.
- Complying with Global Regulations: Laws like the GDPR (EU) and CCPA (California) mandate how organizations collect and handle personal data. Adhering to these laws protects both individuals and businesses from legal risks.
- Ethical considerations: Beyond legal compliance, respecting user privacy is a matter of ethics. Data handling by organizations needs to be transparent, fair, and accountable.
Who Collects Our Data and Why?
Data is collected by a wide range of organizations for different purposes which include:
- Companies and Organizations: Businesses gather user data to understand customer behavior, improve products, and deliver customized services. This is mainly common in sectors like app development, where data insights guide feature improvements and user experience optimization.
- Advertisers and Marketers: They collect demographic and behavioral data to create targeted ad campaigns, improving engagement and return on investment.
- Social Media Platforms: These platforms collect user information, interactions, and preferences to increase engagement, personalize content, and drive advertising revenue.
- Governments and Public Institutions: Government bodies collect data for public safety, law enforcement, policy planning, and resource allocation.
- Service Providers: Internet and telecom companies gather data to manage billing, monitor service performance, and optimize network operations. Given how much personal data is collected, it’s vital to know how to protect our information.
Read More: Biggest Cybersecurity Threats And How to Protect Yourself
Difference Between Data Privacy and Data Protection
Data Privacy is about rights and control. It controls who has access to your data and under what conditions. It focuses on policies and user expectations regarding the use of their personal information.
Data Protection is the organizational and technical steps taken to protect data from theft, corruption, and unauthorized access. This includes firewalls, access controls, encryption, and frequent security assessments.
Data Privacy vs Data Protection
| Aspect | Data Privacy | Data Protection |
| Definition | Individual rights and expectations about the collection and use of personal data. | The methods and strategies used to protect data from unauthorized access or breaches. |
| Focus Area | Refers to who is authorized to access the data. | Refers to how data is secured from threats and risks. |
| Objective | To ensure that individuals have control over their personal data. | To prevent unauthorized access, misuse, loss, or theft of data. |
| Concerned With | Legal rights, consent, transparency, and data usage policies. | Encryption, firewalls, access controls, and cybersecurity measures. |
| Example | Ensuring users agree before their data is shared with third parties. | Adding security protocols to secure stored user data from hackers. |
| Legal Frameworks | Guided by privacy laws like GDPR, CCPA, etc. | Guided by information security standards like ISO/IEC 27001, NIST, etc. |
| Enforced By | Data governance departments, legal teams, and privacy officers. | IT security teams, cybersecurity experts, and compliance officers. |
| Measurement | Consent logs, user access controls, and data usage reports. | Security audits, breach incident reports, and technical safeguards. |
Together, privacy and protection form a comprehensive approach: privacy defines the ‘why’ and ‘who’ of data usage, while protection ensures the ‘how’ is secure and compliant.
Key Principles of Data Privacy
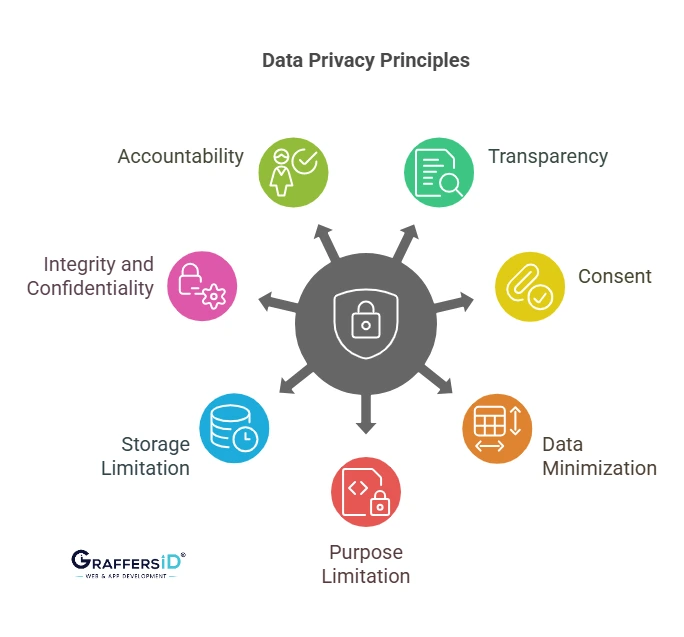
1. Transparency
Transparency means that organizations must inform individuals about:
- What personal data are they collecting (e.g., name, email, location).
- Why are they collecting it (e.g., marketing, service improvement).
- How the information will be shared, kept, and used.
- With whom it will be shared (e.g., third-party services).
This is usually done through a privacy policy, cookie banners, or user agreements. The goal is to help users make informed decisions about sharing their personal information.
2. Consent
Consent ensures that:
- The user’s data is collected only after he/she has agreed to it.
- The consent is willingly given, informed, and accurate—users should know what they are agreeing to.
- Users should also have the option to withdraw their consent at any time.
For example, when a website asks for permission to send newsletters or track cookies, it’s seeking user consent.
3. Data Minimization
This approach refers to collecting only the information required for the task at hand. For example, if a service only requires your email to send notifications, it shouldn’t ask for your address or phone number. Data minimization reduces the risk of breaches and misuse and ensures better compliance with privacy laws.
4. Purpose Limitation
Data should only be utilized for the original purpose for which it was gathered. For example, if you sign up for a webinar, your email should be used only for sending webinar-related information, not for unrelated marketing, unless you give permission. This helps maintain user trust.
5. Storage Limitation
This principle means that personal data should be kept only for as long as required to fulfill its purpose. For example, a company can store customer details while a subscription is active, but should delete them once the user cancels, unless there’s a valid legal reason to keep it.
6. Integrity and Confidentiality (Security)
This focuses on securing data against loss, corruption, breaches, and illegal access. Organizations must use:
- Technical measures (like encryption, firewalls).
- Organizational measures (like access control, staff training).
- Frequent audits and incident response plans.
7. Accountability
Last, accountability means that organizations must:
- Take responsibility for how they handle data.
- Document their data handling practices.
- Be able to present compliance with privacy regulations like GDPR or CCPA.
Data Privacy Challenges in the Digital Era
In the modern era, data privacy is increasingly at risk due to various challenges that arise from the widespread collection, sharing, and storage of personal information. Below are some common cyber challenges:
1. Mass Surveillance
Governments and businesses often conduct large-scale surveillance, which includes collecting and monitoring large amounts of personal data from individuals. Governments may justify such surveillance for national security or crime prevention purposes, while corporations may track consumers for targeted marketing or product recommendations.
However, the extent to which data is monitored can be disturbing, and it raises concerns about how this data is used, stored, and shared.
2. Data Breaches
Data breaches have become a common issue, where hackers or unauthorized individuals gain access to sensitive information. These breaches often affect major companies, exposing personal details such as names, addresses, payment methods, and even health records.
The risk of data being exposed in this way is very concerning, as once personal data is leaked, it can be misused for identity theft, fraud, or other illegal activities.
3. Third-party Sharing
Third-party sharing refers to the practice of companies sharing personal data with other organizations, often without completely informing users or obtaining their consent. Many businesses share data with partners, advertisers, and even unpopular organizations for purposes such as cross-platform targeting or analytics. Users may not be aware of who is receiving their data or how it is being used, creating a major privacy risk.
This can be particularly concerning because it allows data to be shared far beyond the original organization collecting it, and often without the user’s direct consent or awareness.
4. Dark Patterns
Dark patterns are manipulative user interface (UI) designs or strategies used by websites and apps to trick users into giving away more data than they want to share. These unethical practices might involve design choices like making it difficult to deny sharing data, making privacy settings hard to find, or offering “free trials” that automatically renew and continue to collect payment information after the trial ends.
Dark patterns use psychological tricks to convince people to share their information, usually by making it easier to share or collect data than to refuse.
5. Lack of Awareness
A major issue with data privacy is a lack of customer awareness. Many people may not completely comprehend the terms and conditions they agree to when they join up for services or use apps.
For example, consumers may unintentionally allow apps to collect data about their location, contacts, or browsing history without understanding the consequences or what the companies intend to do with that information. Furthermore, users are frequently misinformed by the legal terms used in terms of service and privacy policies, which fail to disclose the full scope of data collection and sharing.
Start-Ups and Data Privacy: A Special Concern
Startups are more at risk to cyberattacks and data breaches than larger organizations because they lack a strong cybersecurity infrastructure and depend heavily on new technology. According to reports, 43% of cyberattacks are targeted at small and medium-sized organizations, including startups.
Startups manage sensitive consumer data such as credit card numbers, medical records, and personal information (birthdates, addresses, and so on), making them main targets for hackers. Data breaches could have a serious negative impact on these businesses.
Common Cyber Risks Facing Start-Ups
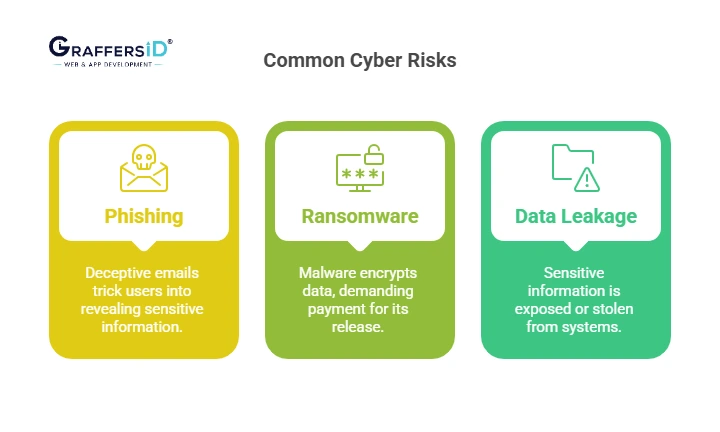
1. Phishing
Phishing attacks, which account for more than 90% of all cyberattacks, trick victims into disclosing personal information such as usernames and passwords, frequently via fake messages and urls.
2. Ransomware
Ransomware is a type of virus that encrypts or locks down a company’s important data until the victim pays a fee. Hackers prefer payments in the form of cryptocurrencies like Bitcoin because they are more difficult to trace than cash or online transactions.
3. Data Leakage
A data leak happens when sensitive information, such as user credentials or payment card information, is accidentally or purposely disclosed to the public.
As a start-up owner, knowing these threats is the first step toward securing your business and protecting your data.
Risks of Sharing Personal Information on Social Media
In today’s digital age, we freely publish personal information on social media and other online platforms without fully understanding the impacts. While these platforms are convenient, they also pose serious hazards to our privacy, security, and financial well-being. Here are some risks of excess sharing:

1. Privacy Invasion
Every time we fill out a form, create a profile, or make online purchases, we leave behind digital footprints. These can be tracked and exploited by advertisers, corporations, or malicious actors. Whether it’s through personalized ads or identity theft, our privacy is constantly at risk online.
2. Identity Theft
Sharing personal information opens the door to identity theft. Cybercriminals use phishing, hacking, and social engineering to gather data for fraudulent activities like stealing money, applying for credit in our name, or accessing our accounts. The consequences can be financially devastating and take years to resolve.
3. Cyberbullying and Harassment
The anonymity of the internet allows for cyberbullying and harassment. By sharing personal details like location or contact information, we make ourselves vulnerable to online predators and malicious individuals who may stalk, threaten, or harass us.
4. Data Breaches
Data breaches are a major concern. Hackers target businesses that keep our private information. A breach can expose us to identity theft, fraud, and other risks, undermining the trust we place in these services to protect our information.
5. Reputation Damage
The internet has a long memory. Once personal information is online, it’s nearly impossible to erase. Careless posts or images can resurface years later, potentially damaging our reputation and credibility in professional or personal settings.
6. Targeted Advertising and Manipulation
The personal data we share feeds algorithms that power targeted advertising. While it may seem harmless, these practices can erode our autonomy and influence our decisions, often without us realizing it. Personalized content can even be used to manipulate opinions or push propaganda.
7. Legal and Regulatory Risks
Online sharing of private information can sometimes lead to legal problems. Violating privacy laws or inadvertently disclosing confidential data can result in fines or legal action. It’s important to be aware of the legal implications of oversharing.
How to Protect Your Privacy on Social Media
To safeguard your privacy, exercise caution with the information you share. Adjust your privacy settings to control who sees your posts, limit personal details, and be selective about what you disclose. Using privacy-enhancing tools like VPNs and encrypted messaging apps can further protect your data.
In the digital age, discretion is essential. By being mindful of what we share, we can navigate the online world more securely and protect our personal information from potential risks.
Read More: Boost Your Startup Cybersecurity with These Powerful Tips
Best Practices for Ensuring Data Privacy
To ensure the security and privacy of your data, it’s essential to implement robust practices that mitigate the risk of data breaches and unauthorized access. By following these practices, you can significantly enhance your data protection measures. Here are some best practices:
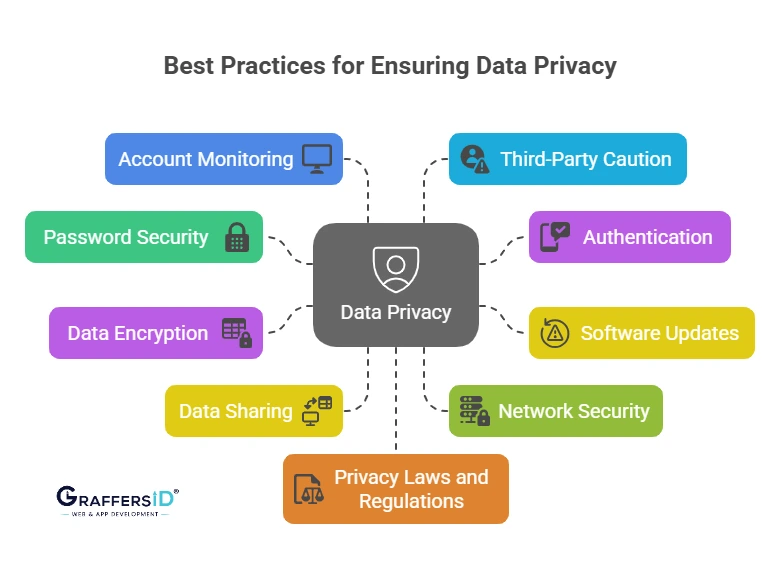
1. Use Strong, Unique Passwords
- Strong passwords are your first line of defense against unauthorized access. Use a combination of letters (upper and lowercase), numbers, and symbols. Avoid using easy-to-guess passwords like “12345678” or “password.”
- Consider using a password manager to store complex passwords securely, so you don’t have to remember them all.
2. Enable Two-Factor Authentication (2FA)
- Two-factor authentication adds an extra layer of security by requiring you to verify your identity using a second method (e.g., a code sent to your phone) in addition to your password.
- Enable 2FA on all your accounts where possible, especially for critical services like email, banking, and social media.
3. Keep Software and Systems Updated
- Regularly update your software, applications, and operating systems. Developers frequently provide updates to address issues and enhance security features.
- Enable automatic updates wherever possible to ensure you’re constantly protected from the latest threats. If you still have downloaded malware that endangers your data, click here to see how to remove it.
4. Encrypt Sensitive Data
- Data encryption ensures that even if your data is intercepted or accessed by unauthorized individuals, it cannot be read without the encryption key.
- Encrypt files, emails, and backups to safeguard your sensitive information, especially for businesses dealing with customer or financial data.
5. Limit Data Sharing
- Pay close attention to the information you post online, especially on public forums and social media. Avoid posting sensitive personal information like your full name, address, phone number, or financial details.
- For businesses, only collect the data that’s necessary for your operations and ensure that it’s stored securely.
6. Use Secure Networks
- Avoid using public Wi-Fi networks to access sensitive data. Public networks are more vulnerable to attacks, making it easier for cybercriminals to intercept your data.
- Use a VPN (Virtual Private Network) to encrypt your internet traffic when accessing sensitive data over any network, including public Wi-Fi.
7. Monitor Your Accounts and Devices
- Check your social media accounts, credit reports, and bank accounts frequently for any unusual activity. Early detection can help you mitigate potential damage from identity theft or fraud.
- Install anti-malware software to protect your devices from malicious attacks.
8. Be Cautious with Third-Party Apps and Services
- Be selective about the third-party apps and services you use. Before granting access to your data, carefully read their privacy policies and permissions.
- Revoke access to apps and services that you no longer use or trust.
9. Educate Yourself and Your Team
- Stay informed about the latest web development trends, shaping data privacy regulations and security threats. Cybersecurity best practices evolve quickly, so continuous learning is key to protecting yourself.
- If you run a business, regularly educate your employees on data privacy and security best practices. Ensure that they understand the importance of safeguarding sensitive information.
10. Adhere to Privacy Laws and Regulations
- Familiarize yourself with data privacy laws like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act). Ensure that your data practices comply with applicable regulations, especially for businesses that handle customer data.
- Implement privacy policies that respect the rights of individuals and ensure transparency about how data is collected, used, and stored.
Data Protection Regulations and Compliance
As the digital landscape continues to evolve, data privacy and protection have become top priorities for businesses and individuals alike. Governments worldwide have enacted various regulations to safeguard personal information and ensure that businesses respect users’ privacy rights. Some important key regulations to keep in mind are:
1. General Data Protection Regulation (GDPR)
The GDPR, introduced by the European Union in 2018, is one of the most comprehensive data protection regulations globally. It applies to businesses that collect or process personal data of individuals located in the EU, regardless of where the company is based.
Key Features:
- Consent: Organizations must obtain clear, explicit consent from individuals before processing their personal data.
- Rights of Individuals: Individuals have the right to access, rectify, delete, and restrict the processing of their data. They also have the right to object to certain types of data processing and to data portability.
- Data Breach Notification: Businesses must notify authorities and affected individuals of a data breach within 72 hours.
- Penalties: Non-compliance with the GDPR can result in hefty fines of up to 4% of global annual turnover or €20 million (whichever is greater).
2. California Consumer Privacy Act (CCPA)
The CCPA, enacted in 2020, applies to businesses operating in California or those that collect personal data of California residents. The law is designed to provide more control over personal data to California residents.
Key Features:
- Right to Know: Consumers can request businesses to disclose the personal data they collect, the purpose of its collection, and how it is used or shared.
- Right to Delete: Consumers have the right to request the deletion of their personal data, subject to certain exceptions.
- Right to Opt-Out: Consumers can opt out of the sale of their personal information to third parties.
- Non-Discrimination: Businesses cannot discriminate against consumers for exercising their rights under the CCPA.
- Penalties: The CCPA allows for fines of up to $2,500 per violation and $7,500 per intentional violation.
Conclusion
The digital world is convenient, but there are some drawbacks. Data privacy is more than a technological requirement; it is a fundamental human right. Individuals must educate themselves, use privacy-enhancing methods, and exercise their rights. As organizations, particularly start-ups, it is important to integrate privacy into the design of their products and services.
Data privacy is everyone’s responsibility. Only through community understanding and action can we create a safer digital future in which innovation and privacy exist together.
At GraffersID, we specialize in developing robust and secure websites and applications that prioritize the safety of your data and the privacy of your users. We follow industry best practices, employing the latest security measures and encryption technologies to safeguard your digital assets from any potential breaches.
FAQs
Q1. How to protect your privacy and data in the digital age?
To protect your privacy and data in today’s digital world, use strong and unique passwords, enable two-factor authentication, keep your software updated, and regularly check and adjust your privacy settings across devices and platforms.
Q2. How can we protect our data and privacy?
We can protect our data and privacy by only sharing personal information with trusted sources, avoiding suspicious links or downloads, and reviewing app permissions frequently. It’s also important to back up your data securely and be careful about what you share online.
Q3. What are the 7 data protections?
The seven data protection principles under GDPR are: collecting data lawfully, fairly, and transparently; using it only for specific, legitimate purposes; collecting only the minimum amount needed; keeping it accurate and up to date; storing it only as long as necessary; protecting it from unauthorized access or breaches; and being accountable for how data is managed.
Q4. What is the difference between data privacy and data protection?
Data privacy refers to the right of individuals to control how their personal information is collected, used, and shared. Data protection, on the other hand, involves the tools, policies, and technologies used to secure that data from unauthorized access, breaches, or theft. In simple terms, privacy is about who has access to your data, while protection is about how that data is kept safe.