In 2026, artificial intelligence has moved from a “nice-to-have” feature to the backbone of modern web development. Today’s websites are no longer static digital assets; they are intelligent systems that learn, adapt, and personalize experiences in real time. Users now expect speed, security, relevance, and seamless interactions from the very first visit, and traditional web development approaches are struggling to keep up.
AI-powered web development enables businesses to build self-optimizing, data-driven websites that evolve with user behavior and market demands. From automating coding and testing to delivering hyper-personalized user journeys and predictive performance optimization, AI is redefining how digital products are designed, launched, and scaled.
Understanding how AI transforms web development is essential to reducing time-to-market, improving conversion rates, strengthening security, and building a future-ready digital platform.
This guide explores how AI is reshaping web development in 2026, the tools driving this transformation, real-world use cases, and how forward-thinking organizations can leverage AI to build smarter, faster, and more scalable web experiences.
What is AI in Web Development?
AI in web development means using artificial intelligence technologies, such as machine learning (ML), natural language processing (NLP), predictive analytics, and intelligent automation to build, manage, optimize, and secure websites and web applications more efficiently.
Instead of relying only on fixed rules and manual processes, AI-powered web systems analyze real-time data, user behavior, and performance patterns to continuously improve how a website functions and how users experience it. This allows websites to become smarter over time, adapting content, layout, performance, and security automatically based on how users interact with them.
In 2026, AI is used across the entire web development lifecycle, including:
-
Design and UI/UX optimization based on user interaction data
-
AI-assisted coding and testing to reduce errors and speed up development
-
Personalization engines that tailor content and user journeys in real time
-
Predictive analytics to improve conversions and engagement
-
AI-driven security to detect threats and prevent attacks proactively
A collection of excerpts from the latest mentions in leading tech magazines highlights how intelligent software solutions are reshaping digital workflows. When developers encounter performance slowdowns on resource-constrained systems, smart optimization tools can automatically clear unnecessary files, improve system responsiveness, and even identify potential security risks, helping maintain a clean, efficient, and secure development environment.
Simply, AI transforms websites from static digital platforms into intelligent, self-optimizing systems that evolve with user needs and business goals, making them faster to build, easier to scale, and more effective at driving results.
Key Benefits of AI in Web Development in 2026
Artificial intelligence is transforming web development from a manual, code-heavy process into a faster, data-driven, and highly adaptive workflow. In 2026, businesses adopt AI not just for efficiency, but to gain measurable advantages in speed, cost, performance, and decision-making.
1. Faster Development and Reduced Costs
AI significantly reduces development time by automating repetitive and time-consuming tasks across the web development lifecycle.
Key benefits include:
-
Automated code generation and auto-completion, which speed up development and reduce human errors
-
AI-powered testing and bug detection, identifying issues earlier in the development cycle
-
Reduced manual effort in maintenance, refactoring, and updates, lowering long-term operational costs
This enables faster time-to-market without compromising code quality or scalability.
2. Highly Personalized User Experiences at Scale
AI enables websites to dynamically adapt to each user in real time, creating experiences that feel relevant and intuitive.
How AI improves personalization:
-
Dynamic content delivery based on user behavior, preferences, and intent
-
Personalized product, content, or service recommendations
-
Context-aware UI and UX, adjusting layouts, messaging, and interactions automatically
Personalization at this level increases engagement, retention, and conversion rates.
3. Improved Website Performance and Reliability
In 2026, website performance is continuously optimized using AI-driven monitoring and prediction systems.
AI improves performance by:
-
Predictive performance monitoring, identifying slowdowns before users notice
-
Proactive issue detection, preventing downtime and crashes
-
AI-assisted optimization for speed, scalability, and responsiveness across devices
This ensures consistent performance even during traffic spikes or feature rollouts.
4. Better Business Decision-Making with Real-Time Data
AI transforms raw website data into actionable business intelligence that leaders can use to optimize growth strategies.
Business-focused advantages include:
-
Data-driven UX improvements based on real user interactions
-
Predictive analytics for conversions, churn reduction, and customer journeys
-
Real-time insights that support faster, more confident decision-making
This shifts web development from execution-focused to outcome-driven.
AI Tools Transforming Modern Web Development in 2026
Artificial intelligence now powers every stage of modern web development from design and coding to personalization, security, and performance optimization. Instead of building static websites, businesses are creating intelligent digital platforms that continuously learn, adapt, and improve.
Below are the key AI-powered technologies shaping web development in 2026.
1. AI-Powered Design and UI/UX Tools
AI-powered design tools help web teams move faster while maintaining design quality, accessibility, and brand consistency.
What AI Design Tools Can Do?
AI design assistants can:
-
Automatically generate responsive layouts for desktop, tablet, and mobile devices
-
Recommend design systems, color palettes, and typography based on brand identity
-
Optimize UI components for usability, accessibility, and user engagement
-
Identify UX friction points using behavioral data
Why This Matters for Businesses?
-
Faster design-to-development cycles
-
Consistent UI across large web platforms
-
Better accessibility compliance
-
Improved user retention and engagement
AI doesn’t replace designers; it augments creativity by eliminating repetitive layout and styling work.
2. AI-Assisted Coding and Software Development
AI-assisted development tools have become core to modern engineering workflows in 2026.
How Does AI Help Web Developers?
AI coding tools support developers by:
-
Auto-completing and generating clean, reusable code snippets
-
Detecting bugs, logic errors, and security vulnerabilities early
-
Refactoring legacy codebases for better performance and readability
-
Summarizing large codebases for faster onboarding and collaboration
Human Oversight Still Matters
While AI accelerates development, human developers remain essential for:
-
System architecture and scalability decisions
-
Complex business logic
-
Security and compliance requirements
Read More: UI vs UX Design in 2026: Key Differences, Examples, and How AI Is Transforming Digital Experiences
3. Predictive Analytics for Personalized Customer Experience
Predictive analytics enables websites to anticipate user needs instead of reacting to them.
What Does AI Analyze?
AI-driven analytics systems analyze:
-
User demographics and location
-
Browsing and navigation behavior
-
Interaction history and engagement patterns
-
Purchase and conversion data
How Do Businesses Use These Insights?
With predictive analytics, websites can:
-
Personalize content in real time
-
Predict user intent and next actions
-
Increase engagement, retention, and conversion rates
Real-World Examples
-
Product and content recommendations
-
Personalized dashboards and landing pages
-
Targeted offers and marketing messages
As a result, websites evolve into intelligent, conversion-focused digital ecosystems.
4. AI Chatbots and Voice Assistants for Websites
Role of NLP in Web Interactions
Natural Language Processing (NLP) enables websites to understand, interpret, and respond to human language naturally.
What Do AI Chatbots and Voice Assistants Do?
-
Provide 24/7 customer support
-
Handle multiple conversations simultaneously
-
Learn and improve responses over time
-
Reduce workload on human support teams
Business Impact
-
Faster response times
-
Higher customer satisfaction
-
Lower operational costs
-
Scalable customer engagement
Read More: AI Assistants vs. AI Agents (2026): Key Differences, Features, and Use Cases Explained
5. AI and Voice Search Optimization
Voice search continues to grow rapidly, with devices like Alexa, Siri, and Google Assistant becoming part of everyday life.
How Does AI Improve Voice Search?
AI enables voice search optimization by:
-
Understanding conversational and long-tail queries
-
Interpreting intent, context, and accents
-
Delivering direct, accurate, spoken answers
Why Voice Search Matters in 2026?
Optimizing for voice search helps websites:
-
Increase organic visibility in AI-driven search
-
Improve accessibility for all users
-
Capture high-intent, action-oriented queries
6. Machine Learning in the Web Development Lifecycle
Machine learning supports every phase of modern web development.
Design and Prototyping
-
Auto-generated UI templates
-
Brand and design consistency enforcement
Development and Testing
-
Code optimization suggestions
-
Predictive testing and error detection
Deployment and Maintenance
-
Automated deployment workflows
-
Performance, uptime, and anomaly monitoring
Machine learning doesn’t replace developers, it amplifies productivity, accuracy, and speed.
Read More: AI in Marketing: AI Marketing Platforms, Ethics, Best Practices in 2026
7. AI-Driven Content Creation and SEO Optimization
AI plays a major role in content and search optimization strategies in 2026.
AI for Content Creation
AI tools are used for:
-
Article and landing page generation
-
Image, video, and media creation
-
Grammar, tone, and readability improvements
-
Multilingual translation and localization
AI for SEO and AEO (Answer Engine Optimization)
Modern AI SEO tools help with:
-
Keyword research and semantic clustering
-
Search intent and user journey analysis
-
Competitor performance benchmarking
-
Optimization for AI Overviews, featured snippets, and zero-click results
This ensures content performs well across traditional SERPs and AI-powered search engines.
8. AI-Powered Web Security in 2026
With rising cyber threats, AI has become a critical security layer for modern websites.
How AI Improves Website Security?
AI-driven security systems:
-
Detect threats and anomalies in real time
-
Identify suspicious behavior patterns
-
Protect sensitive user and business data
-
Prevent fraud using behavioral authentication
AI security solutions balance strong protection with a smooth user experience.
9. AR, VR, and Immersive Web Experiences
AI accelerates the adoption of immersive technologies in web development.
Augmented Reality (AR)
-
Product visualization for eCommerce
-
Remote collaboration and interactive training
Virtual Reality (VR)
-
Immersive real estate tours
-
Virtual classrooms and tourism platforms
These technologies redefine how users explore and interact with digital products.
10. Mobile-First and AI-Optimized Web Development
In 2026, mobile-first design is mandatory not optional.
How AI Supports Mobile Optimization?
AI helps by:
-
Automatically adapting layouts across devices
-
Optimizing performance for mobile networks
-
Enhancing accessibility and usability
Search engines continue to prioritize mobile-friendly, AI-optimized websites, making this essential for visibility and rankings.
Challenges of Using AI in Web Development in 2026
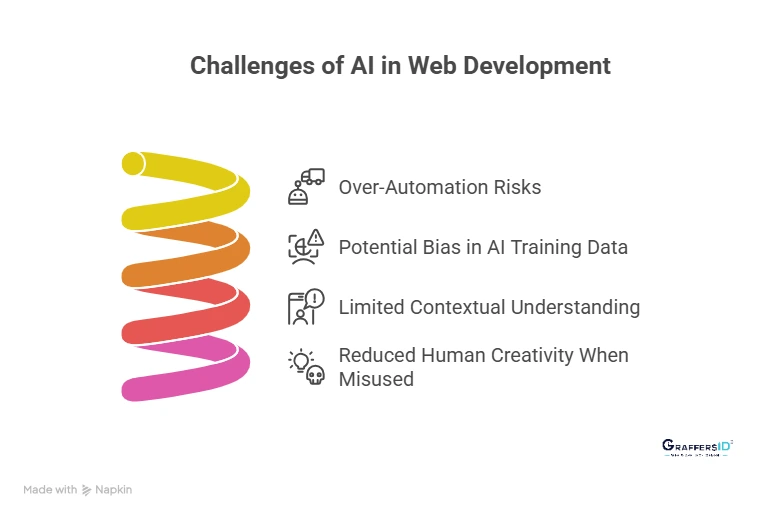
- Over-Automation Risks: Excessive reliance on AI can lead to generic designs and logic-heavy issues, making websites feel less human and strategically misaligned.
- Potential Bias in AI Training Data: AI systems depend on historical data, which can introduce bias into design, personalization, and decision-making if datasets are incomplete or skewed.
- Limited Contextual Understanding: AI may struggle to interpret complex business goals, emotional intent, or nuanced user behavior, leading to inaccurate recommendations.
- Reduced Human Creativity When Misused: When AI replaces creative thinking instead of supporting it, websites can lose originality, brand voice, and emotional connection.
AI delivers the best results when used as a collaborative tool, enhancing human expertise rather than replacing it.
Ethical Considerations in AI-Powered Web Design (What Businesses Must Know in 2026?)
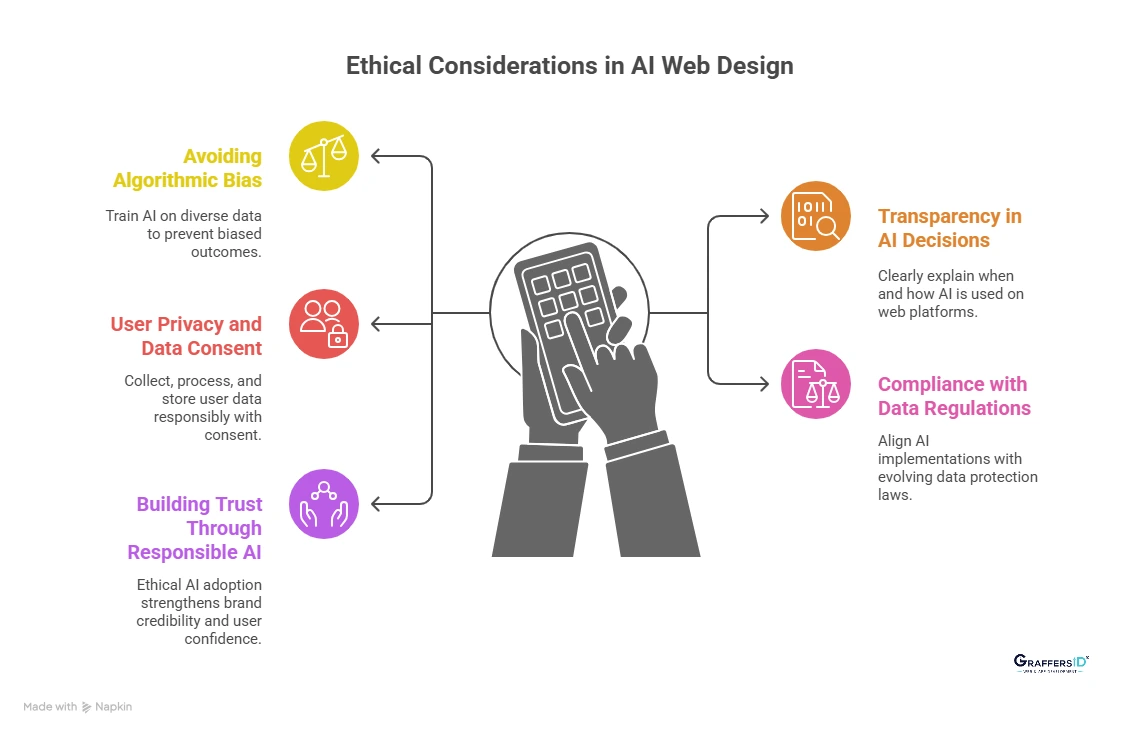
- Avoiding Algorithmic Bias: AI systems must be trained on diverse, representative data to prevent biased outcomes that can impact user trust, accessibility, and fairness.
- Transparency in AI Decisions: Web platforms should clearly explain when and how AI is used, helping users understand automated decisions that affect their experience.
- User Privacy and Data Consent: AI-powered websites must collect, process, and store user data responsibly, with explicit consent and clear privacy disclosures.
- Compliance with Global Data Regulations: AI implementations should align with evolving data protection laws to reduce legal risk and ensure ethical data handling.
- Building Trust Through Responsible AI: Ethical AI adoption strengthens brand credibility, improves user confidence, and supports long-term digital sustainability.
Responsible AI adoption builds trust and long-term value.
Conclusion: Why AI-First Web Development Is the Future
AI and web development are no longer separate disciplines, they are deeply integrated. In 2026, AI enables faster development cycles, intelligent automation, advanced security, and scalable personalization that modern users expect by default. From AI-assisted coding and predictive UX to voice search optimization and real-time threat detection, artificial intelligence is redefining how websites are built, optimized, and evolved.
While AI automates repetitive tasks and enhances efficiency, human developers remain essential for architectural decisions, creative problem-solving, and aligning technology with real business goals. The most successful digital platforms are built on a human + AI collaboration model, where automation accelerates execution and human expertise drives strategy and innovation.
Organizations that adopt AI responsibly and strategically gain a measurable competitive advantage, delivering web experiences that are secure, adaptive, and future-ready, while also performing better across search engines, AI Overviews, and zero-click results.
At GraffersID, we help businesses design and build AI-driven websites and applications that scale with growth.
Contact GraffersID today to create AI-powered, user-centric web experiences designed for performance, visibility, and long-term success in 2026 and beyond.