Cybersecurity in 2026 is no longer just a technical concern; it’s a business survival strategy. With AI-powered cyberattacks, deepfake phishing scams, and supply chain vulnerabilities, the threat landscape has evolved faster than most organizations’ defenses.
Startups, enterprises, and even individuals are now prime targets for increasingly sophisticated attacks that use automation, artificial intelligence, and social engineering. A single breach can lead to massive data loss, financial setbacks, and reputational damage.
The good news? Just as attackers are adopting AI, so are defenders. With the right mix of AI-powered threat detection, zero-trust architecture, and smart security hygiene, you can stay one step ahead.
This blog explores the biggest cybersecurity threats in 2026 and the AI-driven solutions and best practices you can adopt today.
Top Cybersecurity Threats in 2026
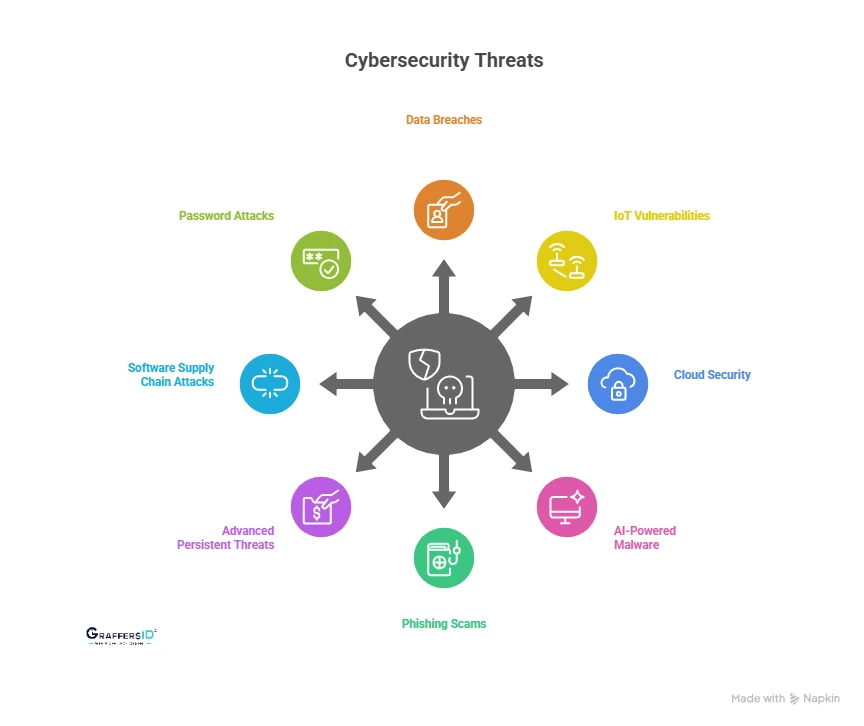
1. Data Breaches & AI-Enhanced Attacks
Data breaches are still among the top threats, but attackers now use AI tools to automate reconnaissance, exploit detection, and credential theft at scale. Companies need to take protection from data breaches seriously. The problem is growing exponentially and is expected to keep growing in the coming years.
-
Trend: Breaches powered by generative AI to craft hyper-personalized phishing.
-
Protection: AI-based anomaly detection, data encryption, and continuous monitoring.
2. IoT Vulnerabilities
IoT technology is becoming more and more popular in the market. It is gradually changing how daily life works. We see IoT devices everywhere, such as in our cars, home appliances, and toys.
However, with a positive change also comes a negative side. With the widespread adoption of IoT from smart homes to connected factories, IoT devices remain weak security points. In 2026, IoT botnets are being used in DDoS attacks, ransomware campaigns, and critical infrastructure hacks.
-
Trend: AI-driven malware targeting IoT ecosystems.
-
Protection: Network segmentation, device authentication, and AI-powered IoT monitoring.
3. Cloud Security & Privacy
Cloud adoption has skyrocketed, but so have cloud misconfiguration and identity-based attacks. Attackers now exploit multi-cloud complexity.
The most important thing to remember when it comes to cloud security and privacy is that your data needs to be encrypted before it travels or is stored on a cloud storage device. Because without encryption, all your data would be susceptible to hacking or theft.
-
Trend: Shadow AI apps running in the cloud without IT approval.
-
Protection: End-to-end encryption, AI-based access controls, and zero-trust cloud governance.
4. AI-Powered Malware & Ransomware
“Malware” is the term for malicious software that infects your computer and does harmful things to you.
Malware may do things like encrypt all your files so you can’t access them, display pop-up messages on your screen, or corrupt your operating system installation.
Traditional malware has evolved into self-learning ransomware that adapts to defenses. Hackers deploy AI-driven ransomware that avoids detection and encrypts entire networks.
-
Trend: Ransomware on IoT devices, autonomous cars, and healthcare equipment.
-
Protection: Behavior-based AI threat detection, immutable backups, and automated recovery plans.
Read More: AI and Cybersecurity in 2026: Emerging Threats, Global Trends & Cybersecurity Best Practices
5. Phishing & Deepfake Scams
Phishing is a type of cyberattack wherein attackers pretend to be someone they are not in order to get you to send them your personal information.
Phishing is no longer just emails; it’s deepfake video calls, AI-generated voices, and synthetic identities. This trend is expected to continue as more devices get connected to the internet.
-
Trend: “Vishing” (voice phishing) powered by cloned voices of CEOs/CFOs.
-
Protection: AI-powered phishing detection, employee training, and advanced email filtering.
6. Advanced Persistent Threats (APTs)
Advanced persistent threats are the most dangerous kinds of cyberattacks. These are a set of methods that allow attackers to hide in the system, to remain undetected and unauthorized while performing malicious activities.
APTs now use AI to blend into normal network traffic, making them harder to detect. These attacks target governments, financial institutions, and enterprises for long-term espionage.
-
Protection: AI-driven endpoint detection and response (EDR), zero-trust frameworks, and real-time threat intelligence.
7. Software Supply Chain Attacks
The Software supply chain attack is a type of attack that exploits the use of software in order to cause harm to the company that owns it. The Software supply chain attack takes place when an attacker intentionally injects malicious code, parts, or services into the software.
The SolarWinds-style supply chain attack remains a huge risk. Attackers now embed malicious code into widely used open-source and AI libraries.
-
Protection: AI-based code scanning, software bill of materials (SBOM), and vendor risk management.
8. Password & Identity Attacks
Password attacks are one of the most basic measures that a hacker would take to break into someone’s account. A brute force attack tries every possible combination of letters and numbers in a password.
Password attacks in 2026 often leverage AI brute force tools and stolen biometric data.
-
Trend: Synthetic identity fraud using AI-generated IDs.
-
Protection: Passwordless authentication, multi-factor authentication (MFA), and identity threat detection.
How to Protect Yourself from Cybersecurity Threats in 2026?
Cybersecurity is a major concern for all organizations, especially in the current digital era. Below, we will explore the various ways to protect oneself from cybersecurity threats.
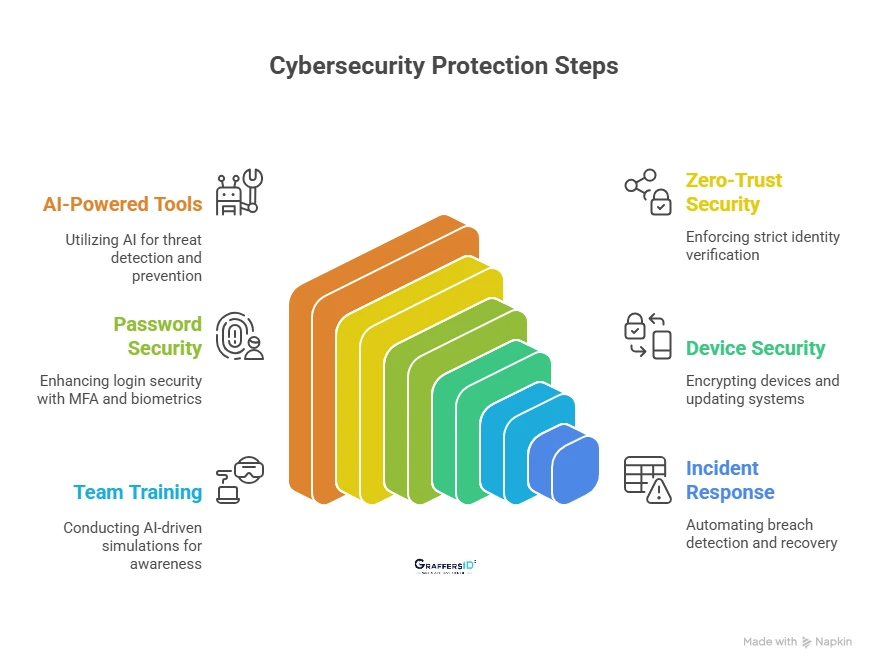
1. Leverage AI-Powered Cybersecurity Tools
- Use AI-driven SIEM tools to monitor system activity and detect anomalies in real time, helping you stop threats before they cause damage.
- Deploy machine learning–based phishing filters that recognize deepfake emails, fake voices, and malicious links to block sophisticated scams automatically.
2. Adopt Zero-Trust Security
- Trust no one, whether inside or outside your network, by enforcing strict identity verification for every access request.
- Implement continuous verification across users, devices, and applications, ensuring attackers can’t move laterally even if they gain initial entry.
3. Strengthen Password & Identity Security
- Switch to passwordless logins, such as biometrics or passkeys, to reduce the risk of stolen credentials being reused.
- Enable multi-factor authentication (MFA) everywhere so even if one credential is compromised, attackers can’t access your accounts.
4. Secure Your Devices
- Encrypt all devices, including smartphones, laptops, and IoT gadgets, to keep sensitive data safe even if hardware is lost or stolen.
- Keep systems updated with AI-powered vulnerability patching tools, which automatically fix security gaps before hackers exploit them.
Read More: Data Privacy in the Digital Age: How to Protect Your Personal Data Online in 2026?
5. Train Teams with AI-Based Simulations
- Regularly run AI-driven phishing simulations to test employee responses against realistic cyberattack scenarios.
- Use gamified cybersecurity training to make awareness programs engaging, improve retention, and reduce costly human errors.
6. Build an Incident Response Plan
- Equip your business with AI-powered forensics tools to analyze and detect breaches faster, minimizing the damage.
- Automate incident response workflows so you can isolate affected systems and recover operations with minimal downtime.
7. Check if You’ve Already Been Involved in a Data Breach
- There is an easy way to find out if your company has been involved in a data breach. Use platforms like “Have I Been Pwned” to check if your email or company data has already been exposed in past breaches.
- If compromised, reset passwords, enable MFA, and monitor accounts closely to prevent attackers from exploiting stolen information.
Conclusion
Cybersecurity is a constant arms race between AI-driven attackers and AI-powered defenders. The future belongs to businesses that proactively integrate AI, automation, and zero-trust models into their security strategies.
At GraffersID, all our developers use company-issued, security-hardened devices with strict access controls and encrypted workflows. Whether you’re building a secure web app, enterprise software, or AI-driven solution, our remote developers in India ensure data safety, compliance, and resilience against modern threats.