In 2026, security is no longer just a safeguard; it’s the foundation of digital trust. Every transaction, healthcare record, SaaS platform, and AI-driven application depends on secure systems to function. But with this dependence comes escalating risk. Cyberattacks, AI-powered scams, and disinformation campaigns are no longer rare events; they are everyday threats that can disrupt businesses, economies, and individual lives within hours.
As artificial intelligence evolves, it is reshaping both the cyber threat landscape and the tools we use to defend against it. While AI enables real-time detection, predictive analytics, and automated incident response, it also empowers attackers with deepfakes, voice cloning, and AI-persona phishing.
This blog explores how AI and cybersecurity in 2026 are redefining global digital security, why protection is now a business-critical priority, and how organizations and individuals can safeguard themselves in an era where being secure means being future-ready.
Digital Security in 2026: Why It Matters More Than Ever
Security in 2026 is no longer about locked filing cabinets or firewalled servers. In today’s hyperconnected world, data, infrastructure, and digital identities are among the most valuable assets anyone owns. A single breach can cripple operations, damage reputations, and cost millions in losses.
For both businesses and individuals, digital security must be treated as a core strategy, not an afterthought. With remote work, global commerce, and AI-driven platforms defining modern life, threats range from ransomware shutting down hospitals to AI-generated scams targeting executives and families alike.
Read More: Data Privacy in the Digital Age: How to Protect Your Personal Data Online in 2026?
Modern Digital Security Threats in 2026
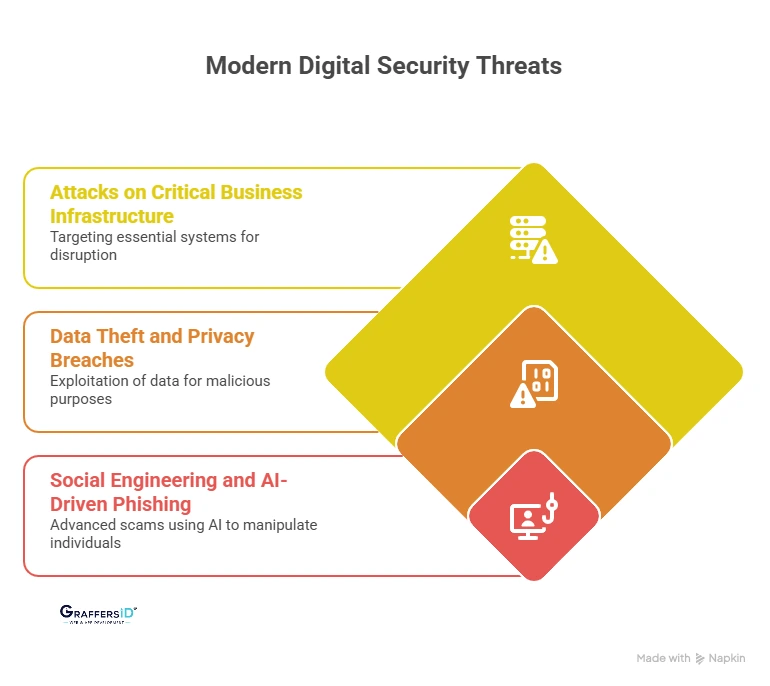
1. Attacks on Critical Business Infrastructure
Cloud systems, banking networks, and SaaS platforms are prime targets. AI-powered malware can disable services at scale, leading to:
- Business shutdowns and disrupted supply chains
- Data leaks impacting thousands of clients
- Mass distrust in online services
2. Data Theft and Privacy Breaches
Hackers target personal data, intellectual property, and corporate databases.
- Behavior prediction: AI models analyze stolen data to anticipate actions.
- Extortion: Confidential data fuels blackmail or fraud.
- Competitive loss: Stolen IP can cripple innovation.
3. Social Engineering and AI-Driven Phishing
Modern scams go beyond fake emails. Attackers now use:
- Cloned voices to impersonate executives
- AI-powered chatbots to deceive employees
- Ransomware-as-a-Service platforms for scalable attacks
Did You Know?
According to Cybersecurity Ventures, cybercrime is expected to cost the world $10.5 trillion annually by 2026, making it the biggest transfer of economic wealth in history.
Top Cybersecurity Threats in 2026
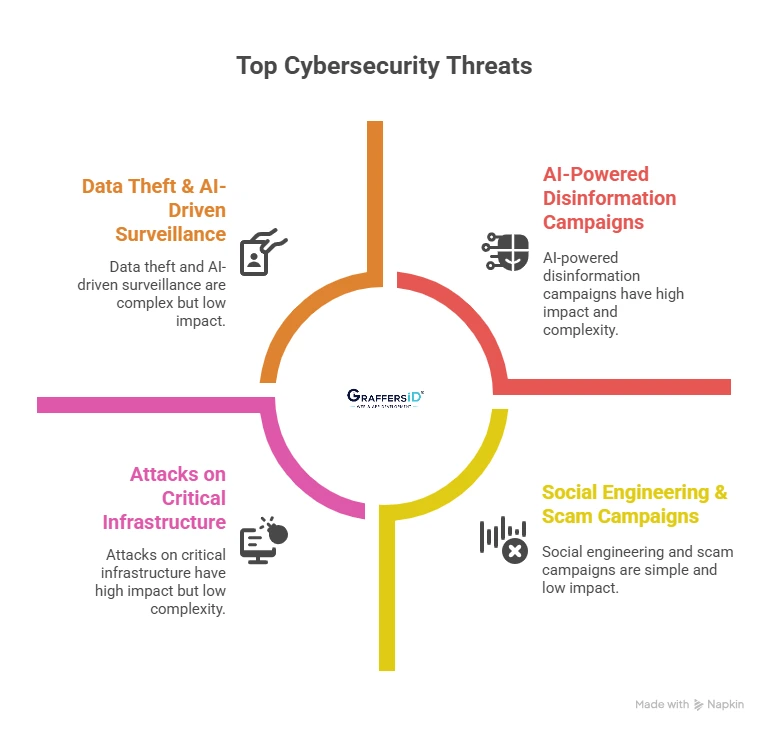
1. Attacks on Critical Infrastructure
Power grids, healthcare systems, airports, and banking networks are top targets. In 2026, AI-powered malware can disable connected devices at scale, leading to:
- Shutdown of communication networks
- Supply chain disruption
- Mass panic and distrust in governments
2. AI-Powered Disinformation Campaigns
Generative AI makes fake news, deepfake videos, and propaganda indistinguishable from reality.
- Public unrest: False reports can trigger riots within hours.
- Erosion of trust: Even genuine government alerts risk being ignored.
- Misguided retaliation: Fake military updates could spark unnecessary escalations.
3. Data Theft & AI-Driven Surveillance
Personal and state data are lucrative targets for cybercriminals and hostile actors.
- Tracking officials: Location leaks can expose strategic movements.
- Behavior prediction: AI models analyze patterns of defense or political leaders.
- Blackmail campaigns: Stolen data can fuel manipulation or extortion.
4. Social Engineering & Scam Campaigns
Attackers use AI-persona phishing (cloned voices, emails, and even video calls) to manipulate individuals into revealing sensitive data.
- Ransomware-as-a-Service (RaaS) marketplaces make attacks more accessible.
- Voice cloning scams have already caused billions in losses in 2024 — and continue to rise.
How AI Improves Cybersecurity and Protects Against Threats in 2026?
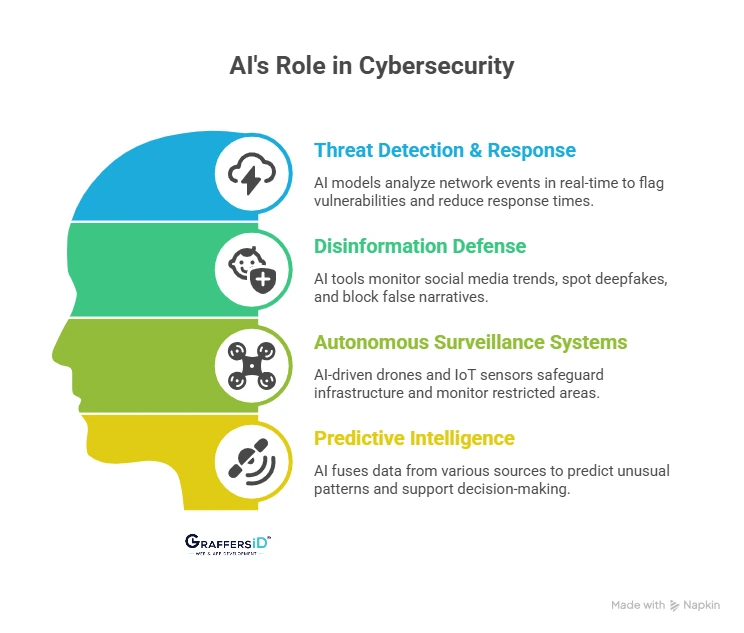
1. AI-Powered Threat Detection & Response
AI models trained on vast datasets of previous attacks can:
- Machine learning analyzes billions of network events in real time.
- Zero-day vulnerabilities are flagged before exploitation.
- Autonomous SOCs (Security Operations Centers) reduce response times from weeks to seconds.
At GraffersID, our expert developers build custom AI-powered dashboards to detect and respond to threats before they escalate.
2. AI for Disinformation Defense
- NLP-based AI tools monitor social media trends to spot disinformation for coordinated propaganda.
- Image & video forensics spots deepfakes instantly.
- Real-time fact-checking blocks false narratives before they spread.
3. Autonomous Surveillance Systems
- AI-driven drones and IoT sensors safeguard infrastructure.
- Motion and thermal analysis monitor restricted areas.
- Facial recognition identifies potential threats in public gatherings.
4. AI for Predictive Intelligence
- Fuses satellite data, CCTV, and communications into one intelligence view.
- Predicts unusual patterns like sudden spikes in network activity.
- Supports faster, data-backed decision-making for enterprises and governments.
Read More: How to Improve Your Startup’s Cybersecurity in 2026: Top Tips to Stay Protected
Role of Startups & Tech Companies in Strengthening Cybersecurity 2026
Innovation often comes from agile startups and IT partners, not legacy defense contractors. In 2026, they are key players in building resilient systems.
- Cloud & Infrastructure Security: AI-powered firewalls, blockchain-based secure communication, and quantum-safe encryption.
- Cyber Defense Innovation: Autonomous malware scanners, endpoint detection, and real-time anomaly detection.
- Rapid Deployment: Startups deliver threat analytics, counter-drone AI, and secure communication tools faster than large vendors.
- Global Collaboration: IT firms provide simulation software, secure SaaS, and on-demand cybersecurity teams.
GraffersID helps global tech firms design AI-powered security solutions resilient against evolving cyber threats.
Cybersecurity Best Practices to Stay Safe Online in 2026
Staying safe means being digitally aware, alert, and prepared with necessary security measures.
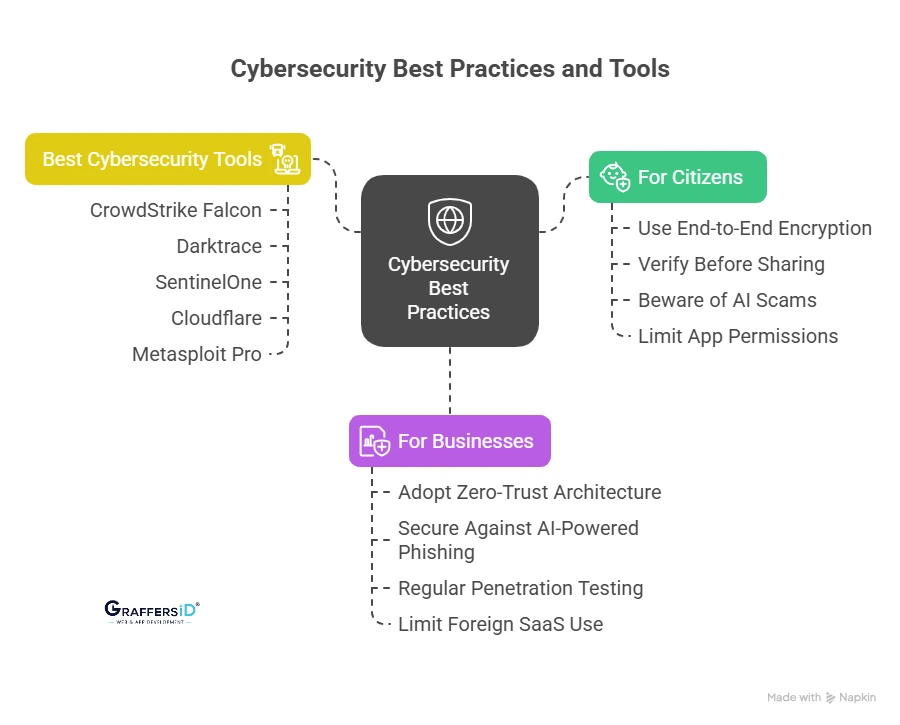
For Individuals:
- Use End-to-End Encryption: Stick to verified platforms like Signal or WhatsApp (with encryption).
- Verify Before Sharing: Use tools like InVID (video checks) and NewsGuard (site credibility).
- Beware of AI Scams: Voice cloning and deepfake messages can impersonate loved ones or officials.
- Limit App Permissions: Avoid apps demanding access to location, mic, or contacts unnecessarily.
For Businesses:
- Adopt Zero-Trust Architecture: Every device, user, and app is verified.
- Secure Against AI-Powered Phishing: Use AI-based email filters and multi-factor authentication.
- Regular Penetration Testing: Simulated cyberattacks expose weaknesses before hackers do.
- Limit Foreign SaaS Use: For sensitive operations, choose neutral or domestic providers.
Best Cybersecurity Tools to Use in 2026
- CrowdStrike Falcon: Advanced threat protection
- Darktrace: AI-based anomaly detection
- SentinelOne: Autonomous endpoint defense
- Cloudflare: DDoS & traffic protection
- Metasploit Pro: Security testing framework
Conclusion
In 2026, digital security is not optional; it’s the backbone of business resilience, innovation, and trust. As threats grow smarter, AI-driven cybersecurity is no longer a luxury but a necessity.
At GraffersID, we build AI-powered solutions that are not only innovative but also digitally secure against evolving cyber threats in 2026 and beyond.