Cybersecurity threats continue to be a major concern for those who use the internet or rely on information systems for their business in 2025. This is because cyberattacks can quickly destroy data and disrupt the services of an organization.
Cyberattacks are now becoming more sophisticated and threatening, so it is important to stay vigilant. We need to understand that there are many different ways that you as an individual can do your part in protecting yourself online.
The Deadly Sins of Cybersecurity
Cybersecurity is a major issue that is present in every industry, not just the tech industry. This is because the digital world has become so intertwined with our real world and cyber attacks are becoming more and more sophisticated. Not knowing what to do can be a deadly sin for cybersecurity. We need to take proactive steps to protect ourselves from cyberattacks in order to avoid any potential disasters.
Cybersecurity is the field of protecting computer systems from the theft, loss, misuse, or improper alteration of data. It takes a lot more than just installing an antivirus program to protect against cyberattacks. There are many types of cyberattacks and methods that can be used to hack into our system.
Top Cybersecurity Threats to Watch Out for
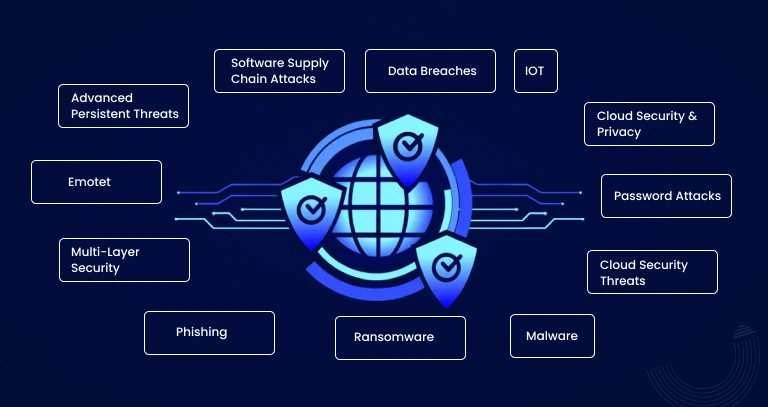
1. Data Breaches
Data Breaches will be a major problem in the coming years. Companies need to make sure that they are staying on top of their data hygiene and security so they don’t suffer the consequences of a data breach.
Companies need to take protection from data breaches seriously. The problem is growing exponentially and is expected to keep growing in the coming years. To think that it would decrease any time soon is naive.
2. IoT
IoT technology is becoming more and more popular in the market. It is gradually changing how daily life works. We see IoT devices everywhere, such as our cars, home appliances, and toys.
However, with a positive change also comes a negative side. The wide adoption of IoT devices has also led to cybersecurity threats that are posing a challenge to many sectors such as energy, healthcare, transportation, and more. According to the report from Gartner, there will be up to 6 billion connected devices in use globally and it is projected that by 2020 there will be 24 billion connected things – this includes appliances, vehicles, buildings, and other objects that have sensors and can collect data.
Read Also: How much will it cost to make an app?
3. Cloud Security & Privacy
The term refers to the security and privacy of the data that is in the cloud (data center) or on a company’s local servers and mobile devices.
The most important thing to remember when it comes to Cloud Security and privacy is that your data needs to be encrypted before it travels or is stored on a cloud storage device. This might be the most crucial aspect of Cloud Security & Privacy because without encryption all your data would be susceptible to hacking or theft.
The two main methods are public key cryptography and symmetric key cryptography. Public Key Cryptography typically uses a combination of an asymmetric key algorithm (public) with a symmetric key algorithm (private). Symmetric
4. Malware
Malware is the term for malicious software that infects your computer and does harmful things to you.
In the 1980s, malware was mostly known as a virus or worm that infected a person’s machine through their email program or their internet browser. In particular, it was often thought of as a nuisance and not much more.
Malware may do things like encrypting all your files so you can’t access them, displaying popup messages on your screen, or corrupting your operating system installation—the list of possible outcomes is limited only by the hackers’ imagination.
5. Ransomware
Ransomware is malicious software that scrambles and encrypts your data so you can’t access it. It then demands a ransom to decrypt it.
Ransomware attacks have now moved from PCs to other devices, such as mobile phones, tablets, and smart TVs. This trend is expected to continue as more devices get connected to the internet. Estimates show that over 50 percent of all ransomware attacks will take place on IoT devices.
6. Phishing
“Phishing” is a type of cyber attack wherein attackers pretend to be someone they are not in order to get you to send them your personal information.
There are many cases of phishing. The most popular form of phishing is via email messages, where these messages look like they come from reputable companies like banks and financial institutions.
The cost of phishing has gone up drastically because more and more people have become so gullible and fall into these traps.
7. Multi-layer security
Multi-layer security is the protection of data by more than one type of security measure. One solution to a problem is not sufficient, so cyber threats have to be guarded against at different levels.
This includes prevention techniques such as firewalls, vulnerability patches, and antivirus software. There are also detection techniques such as Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), which capture information about potential attacks and cut them off before damage can be done.
8. Emotet
Emotet is a Trojan, which uses social engineering and spoofing techniques to steal sensitive data from the user. It has been around since 2014 and it continues to evolve in order to avoid detection.
Malware such as Emotet, Trickbot, and Ramnit are malicious programs that are delivering ransomware, key loggers, Trojans, or other malicious software. These types of malware are common for infecting computers and mobile devices because they can be downloaded in many ways.
Read Also: Start-Up Cybersecurity Tips
9. Advanced persistent threats
Advanced persistent threats are the most dangerous kinds of cyberattacks. They are difficult to detect and often resemble regular computer activity.
Advanced Persistent Threats (APT) are a set of methods that allow attackers to hide in the system, to remain undetected and unauthorized while performing malicious activities. These methods have been studied for years but the term APT was coined by FireEye research in 2004 because they have been observed in attacks from 2001.
10. Password attacks
Password attacks is one of the most basic measures that a hacker would take to break into someone’s account. can be conducted using brute force or dictionary attacks. A brute force attack tries every possible combination of letters and numbers in a password, while a dictionary attack looks up words from the list of commonly used passwords and then tries them out against the target site.
11. Cloud security threats
Cloud security threats are a major concern for businesses that rely on this type of technology. The number of major Cloud security threats will only increase in the future.
Jill Dyché, CEO at Cazena released an analysis of cloud security threats stating that: “Cloud security threats are real, growing and have serious consequences for organizations.”
12. Software supply chain attacks
The Software supply chain attack is a type of attack that exploits the use of software in order to cause harm to the company that owns it. The Software supply chain attack takes place when an attacker intentionally injects malicious code, parts, or services into the software.
Software supply chain attacks are cybersecurity threats in 2025 because more and more hackers are taking control of software creators’ intellectual property and using it for malicious purposes. Therefore, we might see many people becoming victims of this type of cybercrime and it can be very costly for organizations.
What Can You Do to Protect Yourself From Cybersecurity Threats?

Cybersecurity is a major concern for all organizations, especially in the current digital era. This section will explore the various ways to protect oneself from cybersecurity threats.
Organizations need to have a strong cybersecurity infrastructure that can prevent and mitigate any cyber-attacks. The first step is to have an incident response plan in place, which includes having a response team on standby and clear procedures for handling any incidents that might occur.
Check if you’ve Already Been Involved in a Data Breach
There is an easy way to find out if your company has been involved in a data breach. All you need to do is type in a company’s name in the search field. You will see all the articles about current and past data breaches that have happened.
Use the tool “Have I Been Pwned” which lets you put in any email address and it will tell you if that email address has been involved in a data breach. You should do this for every email account that you have, so if your company has been compromised, then any personal information could be at risk too.
Avoid Passwords Mistake
With the recent news about the Facebook data scandal, more and more people are becoming aware of the need to protect their passwords. The most recommended way is to avoid password mistakes and to use strong passwords with symbols and numbers. Some apps like LastPass have full security that uses complex passwords and will auto-fill them when you install the app. But what about apps that aren’t so secure? That’s where a password manager comes in handy. It can generate a strong password for you, sync your passwords across devices, and even include an extra layer of security by automatically locking after too many failed attempts (usually 4).
Here are some mistakes that you should avoid in your passwords:
Reusing a password on different sites
Using a dictionary word as your password
Keeping your password in your phone or computer, so anyone who gets access to them will have access to your account
Secure Your Device
Phones are not just used for communication. In the office, they can be the most valuable piece of software you own. These devices store sensitive data and private conversations.
It is essential to secure devices from cybersecurity threats. This is because compromised phones can lead to larger breaches of data, intellectual property, and customer information.
In addition, recent reports show that cybercriminals are becoming more sophisticated with their attack methods as they adopt new technologies like Voice-over-IP (VoIP) and social media. In order to stay ahead in this game, security professionals have to invest in high-quality cybersecurity training for their staff and be able to respond quickly to changing cybersecurity threats.
Trust No One
The only way to protect yourself from cybersecurity threats is by building a wall of trust around you.
Building a wall of trust around you starts with understanding the threat landscape. Gaining awareness about what to expect and what’s out there is the first step in protecting oneself online.
The biggest online security issue is that people are willing to ignore a potential risk if the reward is worth it, or they don’t know they’re being exploited in the first place.
The only way to protect yourself from cybersecurity threats is by building a wall of trust around you.
Think Before You Click
Cybersecurity threats are getting more and more severe in cyberspace. These cybersecurity threats can come from various sources like malicious links, malicious software, and even third-party apps.
People may want to click on a link if they are curious about what is on the other side. But they should never click any link that they don’t know anything about because there could be malware on it.
You should always think before you click any links to protect your data from cybersecurity threats.
Turn On Two-Factor Authentication
MFA is a security feature that provides an extra layer of protection when you log in. It uses something you know (your password) and something you have (your phone, for example).
When a hacker has your username and password they can easily access your account. With multifactor authentication enabled, they would need to have access to both your phone and your password in order to get in.
The Future is Here and Disturbingly Vulnerable to Digital Attacks
With advancement in technologies, hackers are finding more creative ways to make the cyber world unsafe. Their presence is a constant threat to all the data, and as digitization is becoming more and more prevelent, a lot of people and information is at stake. So, it is important to take every step ensuring your cybersecurity.
At GraffersID, all the developers use company-issued laptops which are protected and secured. We can ensure that there is no breach of data and all of our clients and their information is well protected. So, if you are looking to hire talented remote developers for web and software development, contact us today!