When it comes to outsourcing your Node.js project, there are several security compliances that need to be kept in mind. Node.js helps in building scalable server-side applications and is increasingly gaining popularity. Offshore development teams need to be very vigilant and careful when it comes to security and data protection, as it can affect the projects deeply. In this blog, we will look at effective practices to secure your offshore Node.js projects.
Risks in security
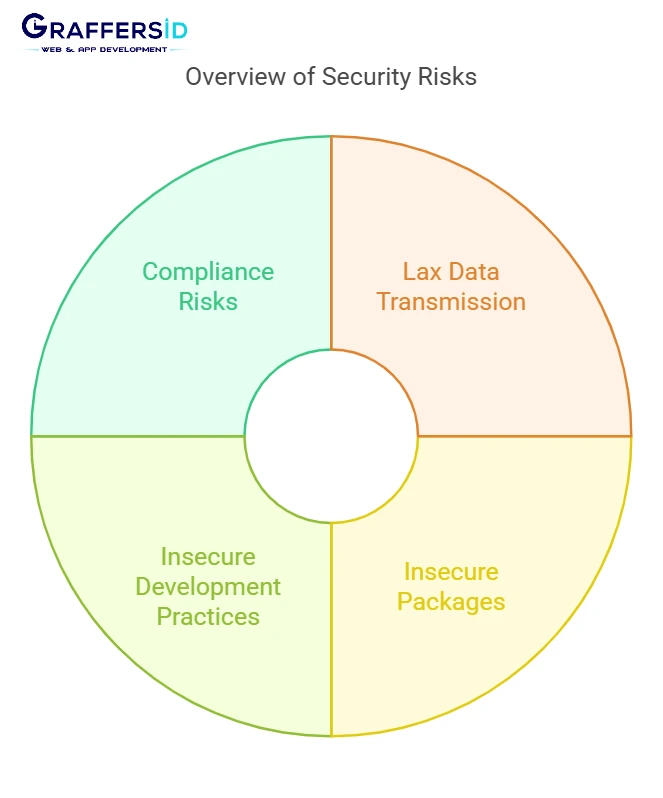
Lax transmission of data
There is a looming risk of data leaks or unauthorized access when companies opt for offshore development, as the project data is being shared with a different location or locations. This can be possible if the channel of transfer is not secured. Cybercriminals or hackers can get their hands on private information if the proper security encryption is not in place, which makes your project vulnerable to several breaches.
Reliance on Insecure packages
The third-party packages that Node.js places heavy reliance on are sometimes not secure- they might not have the proper maintenance, or can introduce vulnerabilities in your project. To the cybercriminals, this is an avenue of attack, which ultimately breaches the application and compromises the data.
Insecure development practices
Sometimes, secure coding practices are not a guaranteed priority with offshore teams. This, in turn, results in certain vulnerabilities like SQL injection, XSS ( cross-site scripting), or unsupported authentication mechanisms in the project.
Compliance Risks
Since offshore development entails cross-border transmission of data, it is important to remain careful regarding the protection regulations in place, like GDPR or CCPA. If not complied with, it can lead to a hefty fine or reputational damage.
Read More: Top 5 AI Coding Assistants in 2026 Every CTO Should Know About
Implementing Robust Security Protocols in Node.js
In order to address these potential risks, it is very important to lay down certain security protocols that can protect your Node.js projects from any possible threat.
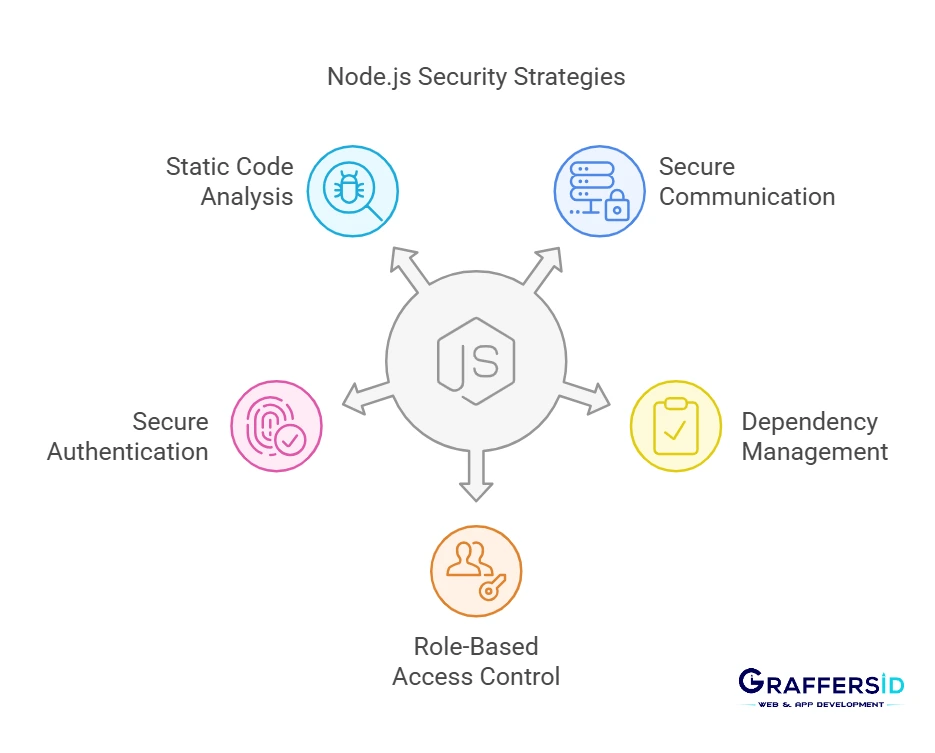
Secure Communication Channels
You need to secure all the communication that takes place between you and your offshore team. To do so, use protocols like HTTPS, SSL/TLS, and secure VPN connections. With this step, you can make sure that the data transmitted over the channel is protected from any sort of interception.
Dependency Management
Snyk or WhiteSource are some tools that can be used to identify and fix vulnerabilities in dependencies. However, you should avoid using packages from untrusted sources and always remember to regularly update your dependencies. To prevent any unintended updates, lock the dependency versions.
Role-Based Access Control (RBAC)
Establish robust RBAC policies within your applications and development environments. Restrict access to sensitive resources according to the principle of least privilege. This guarantees that team members can only access the information necessary for their specific roles.
Secure Authentication
Improve authentication methods by implementing industry standards such as OAuth 2.0 or JSON Web Tokens (JWT). Additionally, incorporating multi-factor authentication (MFA) provides an extra layer of security, making it more difficult for attackers to obtain unauthorized access.
Static Code Analysis
SonarQube, ESLint, and Fortify are static code analysis tools that can be integrated into your development pipeline. The purpose of these tools is to scan your codebase for any sort of potential vulnerabilities. This ensures that your application aligns with secure coding standards.
To protect against DDoS attacks, it’s important to implement rate limiting and request throttling in your Node.js APIs. Using libraries such as Express Rate Limit can help control the number of requests a client is allowed to make within a specific time period.
Data Protection Strategies for Remote Node.js Development
What we can understand so far is that data security is critical in offshore Node.js development. In this entire process, the sensitive process is accessed by the developers and shared across distributed teams. By taking security steps, you are also complying with global security regulations, along with building trust with clients and stakeholders. These are some strategies that can be used to protect sensitive information in remote Node.js development projects.
Encryption at Rest and In Transit
Encryption is a basic element of security that ensures the information remains safe- even if it is being stored or transmitted. This can be done by encryption at Rest with the help of strong algorithms like AES-256, which ensures that even if the data is being accessed, it remains unreadable. Encryption in transit can be done by using secure protocols like HTTPS or Secure WebSocket (WSS). To secure your communication channels, you can use Transport Layer Security (TLS).
Secure Cloud Storage
By adopting security measures for your cloud storage solutions, which provide scalability and convenience, you can prevent unauthorized access. This can be done with the help of trusted providers like AWS S3, Google Cloud Storage, or Azure Blob Storage. You can also use identity and access management policies. Lastly, server-side encryption provided by the cloud provider can be used for additional control over encryption.
Tokenization
Tokenization is a security-enhancing method that replaces sensitive data with unique tokens that are used in place of the original data. The way it works is that it replaces your sensitive information with a non-sensitive counterreplacement token, which is not worth anything and cannot be reversed without access. This process minimizes the exposure to sensitive data and reduces the risk of breaches.
Data Anonymization
Data anonymization can be done to ensure the privacy of user data, transforming it, all of it, while making sure that its utility does not get lost. The way to do this is through using techniques like Mask PII. The tools for this step are called anonymization tools- Faker.js or Mockaroo- to generate dummy data for testing purposes. This step also ensures compliance with certain regulations like GDPR and CCPA.
Regular Backups
Make a habit of backing up your work regularly for data recovery in case of loss of files or cyberattacks. You can automate your backup by using tools like AWS Backup, Google Cloud Backup, etc. You can also opt for storing your data across different locations (geographically). Make sure that your data at rest and in transit is encrypted, and keep testing whether the backup restoration process results in successful saving and restoration whenever needed. Backups are a must in this age of increasing cyber attacks and disruptions.
Regular Security Audits and Compliance in Offshore Teams
To maintain the integrity and security of your Node.js projects when you have opted for offshore development centres, you should instill a habit of conducting regular audits and compliance checks. By doing so, you can proactively identify vulnerabilities, ensure compliance with industry standards, and generate trust in stakeholders by illustrating dedication to strong security protocols.
Conduct Regular Penetration Testing
Also known as ethical hacking, penetration testing involves a simulation of a real-world cyberattack on your device to weed out any vulnerabilities that may exist. You have to basically hire a third-party security expert or deploy penetration testing tools to check the resiliency of your system. The benefits of this test are that you can discover the weaknesses in your system and fix them before an actual attacker breaches the data. Tools for this testing are Burp Suite, Nessus, and Metasploit, to name a few.
Security Checklists and Best Practices
For security best practices, use checklists to ensure complete compliance and protection of your project. Resources like OWASP Top Ten and CIS Benchmarks can be used to guide your security practices. These checklists cover common points of vulnerability. You can also make checklists according to your specific project. Ensure to update your checklists regularly to include new threats and developments.
Logging and Monitoring
Maintaining logs and monitoring systems is important as they can help detect and respond to threats in real-time. The practice of comprehensive logging- logging critical events like login attempts, API requests, database queries, file access, etc., just make sure not to include any sensitive information. Tools like ELK Stack, Splunk, Graylog, etc. can be used to store data. Also, set up automated alerts to notify your team of any possible breaches, login attempts, or suspicious activity.
Incident Response Plan
Having a solid plan in place in case of any security breach can help your team quickly and effectively. To develop the plan, include procedures to identify, contain, eradicate, and recover from breach incidents. Plan drills and training sessions with your offshore teams to ensure everyone is on the same page. Once any incident has taken place, perform a rigorous analysis to identify the main cause and update your security procedures.
Read Also: Business Process Automation- What you Need to Know
Future-Proofing Security Measures in Node.js Development
With new cyberthreats arising daily, adopting proactive strategies for your Node.js projects is important.
AI and Machine Learning for Threat Detection
We have seen how Artificial Intelligence and Machine Learning can transform the way organizations work, specifically in detecting threats and mitigating possible viruses. These technologies can help in real-time analysis with tools like Darktrace, Vectra AI, and CrowdStrike. These tools monitor network traffic, user behavior, and application logs. For defense, use AI-driven systems as they can learn from past data and predict breaches.
Zero Trust Architecture
Under this particular setup, it is assumed that no user or device can be trusted by default- no matter the origin of the network. This approach helps curb the risk of unauthorized access. To do so, there should be strict verification steps for every user and device that is trying to gain access to company resources. Multi-Factor Authentication and device compliance checks are important elements of this model. With this security framework, there can be no unauthorized access to resources and data.
Training and Awareness
Training programs and awareness drives can help empower your offshore teams to identify and recognize risks. This is important as it will ultimately reduce human error, which is a big cause of security breaches. To do this, you can hold workshops and sessions for educating the developers in the latest security practices. Use tools like PhishMe and Confense for attack simulations, like we discussed above. Lastly, the team should be updated regularly about any new vulnerabilities or attacks in the market.
Security as a Service (SECaaS)
In case your organization does not have in-house security experts, you can outsource these particular tasks to security professionals. Security as a service has many advantages, including 24/7 threat monitoring, vulnerability assessments, etc. Outsourcing is a cost-effective measure that gives guaranteed results as the task is allocated to companies that specialise in those fields.
Conclusion
In order to keep an offshore Node.js development project safe, you need a complete and proactive strategy in place. Security and data protection are looming concerns. An organization’s applications and data can easily be kept safe by implementing sustainable security measures that are sustainable. The next steps to be followed are regular audits, checks for compliance, and training programs. Such measures apply further security, leading to confidence in business operations in our increasingly connected world.
At GraffersID, we specialize in secure offshore Node.js development services. Our experienced Node.js developers follow best practices, comply with industry regulations, and leverage the latest tools to deliver secure and scalable applications. Contact us today to future-proof your Node.js projects and achieve your business goals securely!