For building backend APIs and web applications, NodeJS has proven to be one of the best frameworks for runtime JavaScript code bases. Since it is asynchronous, developers have the leverage to develop innovative software solutions with nonblocking events running on a single thread.
Although NodeJS comes with an array of advanced features, there is always a question of security and privacy when considering applications interacting directly with the users. Several cyber crimes and hacking cases have been reported in the last couple of years. In addition, with the increasing pace of digitalization, online safety has become a major concern for many businesses and organizations.
Therefore, if you hire remote NodeJS developers, you should ensure they know the top security practices for making the applications more secure and safer. This article will walk you through the major ways you can implement security in the note application.
Validate SQL Injection Query
In most NodeJS applications, the user sends a request as a database query from the front end to the back end DB. Usually, no validation is used to verify if the query sent to the database from the front end has any malicious content or not.
A hacker can easily manipulate the data in a query and send a command that can wipe out the entire database or clone the tables to get free access to all data.
The best way to prevent such kind of SQL injection query is to validate the user input from the front end. Several types of databases exist where built-in validation is already present to ensure hackers cannot get entry to the server and the on-site database through injection queries.
Prevents XSS Attacks
In a cross-site scripting attack, hackers use JavaScript code to gain access to the main code base of the application and the database. When the person includes the JavaScript code inside a database query, it is executed without restriction.
As a result, unintentional functions are performed on the application that might cause it to shut down completely or allow the hacker to have unhindered access to store user data and sensitive information.
Like SQL injection, the cross-site scripting attack can be prevented by implementing front-end query validation. You should not allow the use of any random database for NodeJS applications as it won’t be able to verify the input and block it if any JavaScript code is presently encoded within the query.
Want to Know the Advantages and Disadvantages of using Node.js
Implementation of a Strong Authentication Layer
Suppose the NodeJS application collects user-sensitive data and stores it in an on-site or cloud server. In that case, it is crucial to ensure you hire NodeJS developers who understand encryption and authentication.
There are several ways of securing an application through multiple layers of authentication. Usually, applications have a simple login or sign-up portal with a user ID and password. These details are easy to hack and therefore don’t provide the ultimate security.
You can implement authentication processes like Okta or auth indicated to ensure the application is fully secured. This will generate a push notification on the mobile either as a confirmation message or a one-time password.
Either way, only the user can access the application because, without the password or the confirmation, the application won’t allow any other person access.
Practical Error Handling Logic
Sometimes, errors are encountered when a code is executed, or an API is run. When you check the log from the back end, you get the full stack dress of the defect, comprising the packages, path, process services, line numbers, functions, and so on where the error has occurred. These information pieces are necessary for a developer to take the debug and check the root cause.
However, it is not of any use to a user. Therefore, when you apply logic in the code for error handling, ensure the error message is abstracted, and only a certain portion is shown to the users.
Similarly, ensure you wrap all the routes to prevent the application from crashing if it encounters any error from the front-end requests. As a result, hackers won’t be able to send any request that can cause your application to shut down completely.
Schedule Automatic Scanning For Vulnerabilities
The NodeJS platform comes with hundreds of built-in libraries and code snippets. You include them in your code base to reduce effort and time because you don’t have to write everything from scratch.
However, there is one problem in terms of security. As the library packages and functions were coded by someone else, you don’t have the guarantee that they are completely secured and won’t open a back door for the hackers.
This is why scheduling automatic scans for code vulnerabilities is crucial when dealing with NodeJS applications. The testing will provide a detailed insight into the app’s health, letting you know if there is any vulnerability in the code which can allow easy access to the hackers.
In addition, you won’t have to wait for a data breach to understand whether any back door is open in the encryption layers or not.
Learn More Is NodeJS Used for Frontend or Backend?
Implement The Use of Security Linters
Security linters are almost like error catchers you can implement during code development. For example, when you write a syntax wrong, the NodeJS framework instantly notifies you about the error. This way, you don’t have to wait for the compilation to happen to identify where the error is and understand the root cause.
Similarly, instead of waiting for the scheduled automatic vulnerability scan to run, you can take the security to the next level by implementing linters. These filters notify you about any erroneous or unsafe code used during the development. As a result, you can easily remove or modify that block to make the statements safer and less vulnerable to attacks.
Make the Configuration Files Transparent
When you hire remote NodeJS developers, you should ensure they have complete knowledge about configuration files and their safety. These files have details about how you configured the application, the orchestrated workflow, integration details, environment data, source code, and so on.
In most cases, developers used to store the configuration files in unsecured repositories. As a result, hackers could easily access these files and know everything about the back end of your application.
Therefore, you should not hide any secrets in the configuration files. Instead, you can implement the concepts of continuous integration and continuous deployment to ensure the coded secrets stored in the config files are integrated properly and deployed regularly.
Orchestrate Production Security For a Node Application
Last but not least, you have to implement appropriate security measures for production. Once the node application is developed, you must release the code to merge with the production environment. Since it interacts with the users upfront, you should put multiple validation layers so that no front-end query or request can trigger any unwanted JavaScript code or database query.
Also, every developer must close all possible backdoors and prevent data leakage. There is nothing like a 100% secure application, but you can achieve 99% security by implementing some of these techniques in the production environment of the node application.
How can to secure Node.js applications against common vulnerabilities
Now let’s understand how you can secure your Node.js application against common vulnerabilities. By following these best practices, you can protect your application and user data from potential threats.
1.Keep Dependencies Up-to-Date
One of the primary sources of vulnerabilities in Node.js applications is outdated dependencies. Regularly update your project’s dependencies, as developers often release patches and updates to fix security issues. Utilize tools like npm audit to check for known vulnerabilities in your project’s dependencies and address them promptly.
2.Implement Input Validation
Inadequate input validation is a leading cause of security vulnerabilities. Ensure that your application thoroughly validates and sanitizes all user inputs. Use libraries like express-validator to simplify the input validation process and prevent common attack vectors like SQL injection and cross-site scripting (XSS).
3.Avoid Callback Hell with Promises or Async/Await
Callback hell, also known as the “pyramid of doom,” can make your code harder to read and maintain. Using Promises or async/await makes your code more manageable and can help prevent race conditions and callback-related vulnerabilities.
4.Set Secure HTTP Headers
HTTP headers play a crucial role in web security. Configure your Node.js application to set secure HTTP headers, such as Content Security Policy (CSP), X-Content-Type-Options, and X-Frame-Options. These headers can help prevent cross-site scripting attacks and other common web vulnerabilities.
5.Use Authentication and Authorization
Implement strong authentication and authorization mechanisms to control access to your application’s resources. Popular libraries like Passport.js can simplify the authentication process, while access control lists (ACLs) and role-based access control (RBAC) can help manage authorization.
6.Protect Against Cross-Site Request Forgery (CSRF)
To prevent CSRF attacks, use tokens in your forms and APIs. Libraries like csurf can automatically generate and verify these tokens. Additionally, always require the SameSite attribute on cookies to prevent cross-origin requests from potentially compromising your application.
7.Employ Secure Authentication Methods
Avoid storing passwords in plain text or using weak encryption. Instead, use strong, industry-standard hashing algorithms like bcrypt to securely store user passwords. Implement multi-factor authentication (MFA) for an extra layer of security.
8.Logging and Monitoring
Implement comprehensive logging and monitoring for your application. Monitoring tools like New Relic, Sentry, or custom solutions can help you detect and respond to unusual activity or potential security breaches promptly.
9.Regular Security Audits and Penetration Testing
Periodically conduct security audits and penetration testing to identify and address vulnerabilities in your Node.js application. Hiring a professional penetration testing team can help you discover hidden weaknesses.
10.Secure APIs
If your Node.js application serves as an API server, ensure it follows RESTful API security best practices. Implement OAuth 2.0 for user authentication and authorization to protect your APIs from unauthorized access.
11.Deploy a Web Application Firewall (WAF)
Consider deploying a web application firewall (WAF) to provide an additional layer of security. A WAF can filter and block malicious traffic before it reaches your application, offering protection against common attacks such as SQL injection and cross-site scripting.
How to Secure RESTful APIs in Node.js
They enable seamless communication between client-side and server-side applications, making them a fundamental component of the Internet. However, this increased reliance on RESTful APIs also means that securing them is of paramount importance. In this blog post, we will explore various strategies and best practices for securing your RESTful APIs in a Node.js environment.
1. Use HTTPS (SSL/TLS): Secure Sockets Layer (SSL) or Transport Layer Security (TLS) is the first and most fundamental step in securing your RESTful APIs. By encrypting data in transit, you protect it from eavesdropping and tampering. Node.js offers excellent support for HTTPS, and services like Let’s Encrypt make it easier than ever to obtain and manage SSL certificates.
To set up HTTPS in Node.js, you can use the built-in ‘https’ module. Here’s a simplified example:
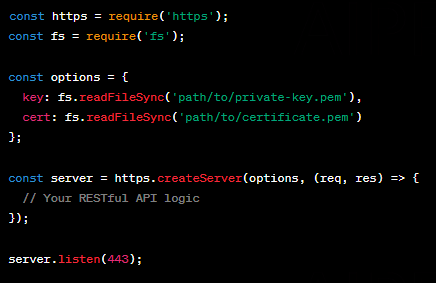
2. Implement Authentication:
a. Token-Based Authentication: Token-based authentication, such as JSON Web Tokens (JWT), is a popular choice for RESTful APIs. In this method, clients receive a token upon successful login, which they include in their requests. The server validates this token for each request.
Here’s an example of using JWT with Node.js and the ‘jsonwebtoken’ package:
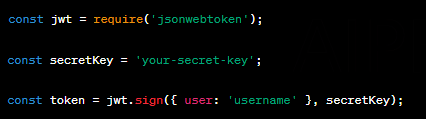
b. OAuth2: OAuth2 is an industry-standard protocol for authorization. It enables third-party applications to access your RESTful APIs on behalf of the user. Implementing OAuth2 in Node.js can be done using packages like ‘passport’ and ‘oauth2orize’.
3. Rate Limiting: To prevent abuse or DDoS attacks on your RESTful APIs, you should implement rate limiting. With rate limiting, you can restrict the number of requests an IP address or user can make within a given timeframe. The ‘express-rate-limit’ package can help you achieve this.
4. Input Validation and Sanitization: Always validate and sanitize user input to protect your RESTful APIs from SQL injection, cross-site scripting (XSS), and other attacks. Using libraries like ‘express-validator’ can simplify this process.
5. Error Handling: Handle errors gracefully and avoid exposing sensitive information. Use custom error messages instead of revealing internal details about your application. You can create a centralized error handler middleware in your Node.js application to achieve this.
6. Cross-Origin Resource Sharing (CORS): Implement CORS to control which domains can access your API. This prevents unauthorized websites from making requests to your API and helps protect against cross-site request forgery (CSRF) attacks.
Here’s an example of enabling CORS with the ‘cors’ package:
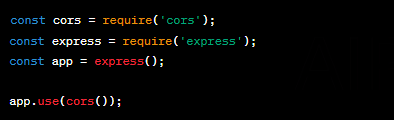
7. API Versioning: Always version your APIs to maintain backward compatibility. This ensures that changes to your API won’t break existing clients and allows them to migrate at their own pace. You can implement API versioning in your routes and controllers.
8. Logging and Monitoring: Implement comprehensive logging and monitoring to keep track of any unusual activities or security breaches. Tools like ‘Winston’ and services like ‘Sentry’ can help with this.
9. Regular Security Audits: Conduct security audits and penetration testing of your RESTful APIs periodically to identify and fix vulnerabilities before they can be exploited by attackers.
10. Keep Dependencies Updated: Regularly update your Node.js and package dependencies to ensure that you are protected against known security vulnerabilities.
In conclusion, securing RESTful APIs in Node.js is a multi-faceted task that involves encryption, authentication, rate limiting, input validation, error handling, and many other considerations. By following these best practices and staying up-to-date with the latest security trends, you can build robust and secure RESTful APIs to protect your data and users. Remember that security is an ongoing process, and vigilance is key to maintaining a strong defense against evolving threats in the digital landscape.
Tools or Libraries Available for Node.js Security Testing
Security is a paramount concern for any web application or server, and Node.js is no exception. As an open-source runtime, Node.js is susceptible to various security risks, including:
- Injection Attacks: Node.js applications can be vulnerable to SQL injection, cross-site scripting (XSS), and command injection, which can have severe consequences if exploited.
- Insecure Dependencies: Many Node.js applications rely on third-party packages from npm, making them susceptible to vulnerabilities. Unpatched or insecure dependencies can introduce significant risks.
- Authentication and Authorization Issues: Weak authentication mechanisms can lead to unauthorized access, compromising the security of your application.
- Data Exposure: Improper data handling can result in sensitive information leakage, potentially harming your users and your organization.
Proactively addressing these vulnerabilities through comprehensive security testing is essential to protect your Node.js applications and the sensitive data they handle.
A Compilation of Tools and Libraries for Node.js Security Testing
- Node Security Project (NSP):
- The Node Security Project provides a command-line tool called
nspfor checking Node.js modules for known vulnerabilities. This tool scans your project’s dependencies and alerts you to any security issues. It is especially valuable in identifying outdated or compromised packages, enabling you to take immediate action.
- The Node Security Project provides a command-line tool called
- OWASP Dependency-Check:
- While not Node.js-specific, the OWASP Dependency-Check is a powerful tool for identifying vulnerable third-party dependencies in your Node.js project. It supports a wide range of package managers, including npm, yarn, and pnpm, making it an indispensable tool for ensuring the security of your application’s dependencies.
- Snyk:
- Snyk is a widely used security tool for Node.js and other ecosystems. It integrates seamlessly with your continuous integration (CI) pipeline and identifies and mitigates vulnerabilities in your application’s dependencies. Snyk also offers insights into license compliance, helping you maintain a secure and compliant codebase.
- Retire.js:
- Retire.js is a simple yet highly effective tool that checks your project’s dependencies for known security vulnerabilities. It’s especially valuable for identifying outdated or risky JavaScript libraries, which are often overlooked sources of vulnerabilities.
- Node.js Interactive Security Testing (NIST):
- Node.js Interactive Security Testing (NIST) is an interactive command-line tool specifically designed for Node.js. This tool allows you to interactively test your Node.js application for security issues. NIST offers a wide range of test scenarios and guides you through potential vulnerabilities, making it an excellent tool for hands-on testing and learning.
- Husky:
- Husky is a Node.js library that helps you set up Git hooks to enforce security policies. For instance, you can use Husky to prevent the commit of known vulnerable dependencies or to run pre-commit security checks, ensuring that your codebase remains secure throughout the development process.
- Node.js Security Scanner (NSC):
- The Node.js Security Scanner (NSC) is an npm package that allows you to scan your Node.js project for vulnerabilities. It’s user-friendly and can be easily integrated into your development workflow, making it a valuable addition to your security testing toolkit.
Hire Dedicated Senior NodeJS Developers From India – How to?
So, you want to hire Senior NodeJS developers for your NodeJS application but do not know how to hire the best NodeJS developers in the Industry. Do not worry, you have landed at the right place.
In this blog, we have covered in detail what it Nodejs, the advantages and disadvantages of NodeJS, How you can hire Senior NodeJS developers, Cost of hiring senior NodeJS Developers.
At the point when you are considering fostering a constant web application that is information escalated.
Nodejs is at present the world’s most mainstream innovation that is opening up boundless vocation opportunities for any developer who is searching for potential growth and development in this field.
Using NodeJS, developers can code various applications, for example, applications for web-based media, texting stages, applications for constant checking, web-based gaming, and instruments for joint effort.
If you a startup planning to develop an application using NodeJS, you can hire NodeJS Developers in India from GraffersID.
In any case, the vast majority commit a new kid on the block error wherein they simply begin learning a language or structure without setting an objective regarding what reason it will serve.
What is NodeJS?

It is an open-source system and a worker-side stage. It reacts to activities produced by the client so it gives an event-driven climate.
NodeJS utilizes offbeat programming which implies that when an undertaking has shipped off the framework, the worker doesn’t trust that API will return information and it doesn’t obstruct it. Its bundle biological system, npm, is the biggest programming library on the planet.
In case you are up to building a constant or streaming web application with different simultaneous associations you’ll profit from Node capacities, particularly as far as proficient execution and simpler advancement measures.
It can turn into a clever decision for API improvement, with its capacity to deal with various demands and scale without a hitch.
Ryan Dahl developed NodeJS in 2009, during the European JavaScript Conference, and in a split second seen as the greatest fit for programming.
Advantages Of Using NodeJS
1. Simplicity of versatility
Nodejs has been viewed as a feasible arrangement with regard to creating adaptable applications. The cross-stage runtime climate has a bunch module and works with load adjusting.
Nodejs permits adding additional assets to the single hubs. These additional assets are added to the current framework as it were.
2. Freedom in Building Apps
Nodejs gives you substantially more space and opportunity to do it your own would prefer. Nodejs is un-opinionated, which means you begin building everything without any preparation.
It can execute essential assignments, however gives you just the absolute minimum from a new introduction, making it less limited.
3. It requires a low expectation to learn and adapt
Utilizing Nodejs for web applications organizations experience every one of the advantages of full-stack improvements, like upgraded efficiency, and capacity to share or reuse the code, just as a smooth trade.
On the off chance that you decide to choose Nodejs, you can profit from the simplicity of sharing very much the same language both on the worker and customer sides.
It eliminates the need to switch between the back-end and front-end and requires fewer designers to keep up with the workers, as you can have one group for the two sides.
Read Also: Deno vs. Node: Which is Better in 2022
4. Request Handling
NodeJS gives a non-obstructing IO framework that allows you to deal with various demands simultaneously. Approaching solicitations are lined up and executed consecutively in a quick way.
Essentially your application will take up substantially less framework RAM, accomplish high adaptability levels, and therefore will perform quicker.
5. Reserving Support
NodeJS upholds the reserving of modules. Consequently, when a NodeJS module is mentioned on the first occasion it is reserved in the application memory.
So next calls for stacking a similar module may not cause the module code to be executed once more.
6. Rich environment
One of the advantages of utilizing Nodejs is its rich environment. Building backend applications has never been simpler with npm, a Nodejs bundle installer that additionally bends over as the commercial center.
7. Lightweight and Extensible
NodeJS depends on JavaScript, which can be executed on the customer side just as on the worker side. Likewise, it upholds the trading of information utilizing JSON, which is effortlessly devoured by JavaScript.
This makes it lightweight when contrasted with different structures. It is additionally the motivation behind why JavaScript, the language for NodeJS wins the clash of prevalence.
8. Cost-productive with full-stack JavaScript
With NodeJS, the designers can compose codes in both frontend and backend in a problem-free way. This is because it allows an opportunity to compose worker-side code in JavaScript for the designers.
Other than this, it makes the course of absolute web advancement quicker without thinking twice about quality.
Disadvantages of NodeJS
1. NodeJS is Poor at Processing Large Data Volumes
In contrast to Python, which is incredible in CPU-escalated and information-based assignments, Nodejs isn’t exceptional in dealing with complex activities.
Its solid suit is the fast handling of various basic solicitations, however, anything convoluted causes delays.
2. Conflicting
NodeJS API has some consistency issues. On the majority of occasions, the new API accompanies many reverse changes, and then, at that point, the developers need to make changes in the code to make it viable.
3. Unstable API
Perhaps the greatest burden of NodeJS is that it needs consistency. Nodejs API changes often, and the progressions are frequently in reverse incongruent.
4. Untidy Syntax
NodeJS is so easy. The language took a ton of provisions from different dialects, and it follows JS standards earnestly.
Notwithstanding, JS is as yet a front-end language, which influences the Node’s backend limits.
Read More: Django vs Node: What to choose
5. It doesn’t uphold multi-strung programming.
Not Suitable for Large and Complex Web Applications. Designers need to confront versatility issues with the offbeat programming models.
6. Not viable with enormous scope applications
NodeJS doesn’t uphold multi-strung programming; this is the motivation behind why it is just liked for lightweight applications. In case you are utilizing it for substantial applications, your decision isn’t right.
NodeJS Developer Roles and Responsibilities
NodeJS development administrations incorporate both front-end and back-end. So regardless of whether you will hire a back-end engineer capable of NodeJS, they ought to have an essential comprehension of the client confronting part of utilization and be prepared to work with front-end components.
The essential focal point of NodeJS experts is the administration of information trade among clients and workers.
In addition, designers work on such issues as making rationale behind applications, building up near-amazing execution, and ensuring that client demands are prepared by the framework.
Read More: What is Node JS used for
Instructions to Hire Senior NodeJS Developer:
1. Framework you’re Requirements
Before you continue to survey what abilities the group ought to have, draft your requirements. Knowing what your venture requires is a simple method to plan something very similar to expected applicants.
2. Picked the Type Of Hiring
- Consultant
- In-house
- Advancement Company
3. Work Experience
In software development, years of experience play an important role. Experienced NodeJS developers can resolve an issue in less time as compared to a newbie. They have tackled such queries in the development process.
4. Programming Skills or The Technology Stack
When you hire a developer for your software development project, check for the additional languages they know about. For instance, If you are hiring a NodeJS developer and a candidate knows any JavaScript should be the right talent.
5. Abilities Apart From Technical Domain
6. Post on Social media such as LinkedIn, Instagram, etc.
Social media is one of the best ways to connect with a large group of people. Nowadays, most of us are using social media.
If a startup or an entrepreneur has a requirement for NodeJS developers and you post it on social media. Interested candidates start to connect with you.
You can ask them for their testimonials, and based on that, you can hire the best talent for your NodeJS project.
7. Shoot Ads on different social media
Different social media platforms, such as LinkedIn, Facebook, Instagram, and others, allow you to place Ads on their platforms.
For that they charge based on the popularity of your keyword, for example, Hire NodeJS Developer is a generic keyword that will cost you more as compared to Hire Senior NodeJS Developer.
These Ads are shown to interested people who are reaching to interested people. You can also add filters such as Age, Gender, Country, and others.
8. Ask reference from your Office team
To Identify and hire the best talent around, you can take references from your team members. If they are in touch with an expert NodeJS developer, they can easily connect you.
Required things to check while hiring a developer:
- Research Well
- Take a look at Their Experience
- Look at Their Communication Skills
- Set Clear Expectations
- Set a guideline: Ability, Programming apparatuses, Advancement measures, undertaking the board, Correspondence
Read More: How to Make a Smooth Transition to Remote Development Team
On Remote Development Teams Or A Freelance Developer:
One of the greatest selling points of an in-house development team is that you can genuinely place everybody in a similar spot, which delivers a ton of elusive advantages culture, faithfulness, simpler correspondence, and so forth.
Besides, employing a rethinking organization is versatile, which implies that you can extend or decrease the size of the group to fit the specific necessities of the venture, in this manner saving assets over the long haul.
Employing a re-evaluated application engineer sorts out the smartest possible solution. The entrepreneur enlists application developers who have utilized distinctly on a legally binding premise.
It’s still more affordable than getting an in-house group, and due to the social scene, the item is better in contrast with employing a single freelancer.
- Use different portals such as Upwork, freelancer
- Hire small start-ups
How to Assess the Skills of Senior Node.js Developers in India
In today’s fast-paced tech industry, finding and hiring top-tier Node.js developers is crucial for building robust and scalable web applications. India has emerged as a global hub for software development, and many talented senior Node.js developers call the country their home. However, assessing the skills of senior Node.js developers can be challenging, as the technology landscape evolves rapidly. In this article, we’ll explore the key aspects you should consider when evaluating senior Node.js developers in India.
-
Understanding the Role of a Senior Node.js Developer
Before delving into the assessment process, it’s essential to understand the role of a senior Node.js developer. Senior developers are expected to have in-depth knowledge and experience in Node.js, a server-side runtime environment built on Chrome’s V8 JavaScript engine. They play a critical role in designing, developing, and maintaining server-side applications using Node.js. A senior Node.js developer should also be proficient in related technologies, such as Express.js, asynchronous programming, and database systems like MongoDB or PostgreSQL.
-
Technical Proficiency
To assess the skills of senior Node.js developers, you must evaluate their technical proficiency. This involves examining their knowledge of core Node.js concepts, including event-driven architecture, modules, and streams. You can use the following methods:
a. Coding Challenges:
Provide candidates with coding challenges or small projects that require them to demonstrate their understanding of Node.js fundamentals. Evaluate their code quality, efficiency, and adherence to best practices.
b. Problem-Solving Abilities:
Ask candidates to solve real-world problems related to asynchronous programming or handling large datasets using Node.js. Evaluate their problem-solving skills and ability to optimize code for performance.
c. Debugging Skills:
Assess their ability to debug and troubleshoot Node.js applications effectively. A strong candidate should be proficient in using debugging tools and diagnosing errors efficiently.
-
Framework and Library Proficiency
Node.js developers often work with various frameworks and libraries to streamline development. It’s crucial to assess a candidate’s proficiency in these tools. Some of the key areas to consider include:
a. Express.js:
Evaluate their knowledge of Express.js, a popular Node.js web application framework. They should be able to create RESTful APIs, handle middleware, and implement routing effectively.
b. npm (Node Package Manager):
Assess their familiarity with npm and their ability to manage dependencies, package.json files, and project structure efficiently.
c. Testing Frameworks:
Determine if they are comfortable with testing frameworks like Mocha, Chai, or Jest. Strong testing skills are essential for maintaining code quality and reliability.
-
Database Proficiency
Senior Node.js developers often work with databases to store and retrieve data. Assess their proficiency in working with different types of databases, such as:
a. MongoDB:
Evaluate their ability to interact with MongoDB, a NoSQL database commonly used with Node.js applications. They should understand schema design, CRUD operations, and indexing.
b. SQL Databases:
Determine if they are familiar with SQL databases like PostgreSQL or MySQL. Assess their ability to write efficient queries and work with ORMs (Object-Relational Mapping) if required.
-
Performance Optimization
A senior Node.js developer should be adept at optimizing the performance of applications to ensure responsiveness and scalability. To assess this skill:
a. Scalability:
Discuss their experience with scaling Node.js applications horizontally or vertically. Ask about load balancing, clustering, and caching strategies.
b. Performance Monitoring:
Inquire about their use of performance monitoring tools like New Relic or Prometheus to identify bottlenecks and optimize code and infrastructure.
-
Soft Skills and Communication
Apart from technical skills, soft skills are equally important, especially for senior developers who often collaborate with cross-functional teams. Evaluate their:
a. Communication Skills:
Assess their ability to articulate complex technical concepts clearly and work effectively with team members, product managers, and stakeholders.
b. Problem-Solving Attitude:
Determine if they can approach challenges with a proactive and creative mindset, seeking innovative solutions.
c. Leadership and Mentorship:
For senior roles, consider their ability to mentor junior developers and lead development teams.

- Pressed For Time
- Lack of Clarity
- Ability of team
- Types of projects worked
- Budget Constraints
- Launch Deadlines
- Lack of Available Talent
Cost To Hire A NodeJS Developer
If you reside in the USA and are looking for local Developers with experience of 3 to 5 years, then hiring a NodeJS developer in the USA can cost you around $80 to $150 per hour. On the other hand, the cost to hire Senior NodeJS developers with 8+ years of experience might be around $200 – $250.
To reduce your software development cost, you can outsource your software project or hire dedicated remote developers according to your project requirements. Several countries such as India, Sri Lanka, and China, have cheap labor costs, and more resources available.
Hiring a dedicated NodeJS developer in India can cost you around $15 to $50 per hour based on years of experience. When you have this agreement, essentially go to the most applicable on the web or disconnected spots and begin looking for the ideal individuals!
The coordination issue with hiring independent or worker application developers as they work distantly. Email and remote coordination are regularly the solitary methods for reaching them. This trouble is additionally compounded on the off chance that they live in various time regions.
When you hire dedicated developers, ensure that correspondence isn’t hampered by this coordination. It’s in every case best to get somebody from your side of the world and concur on explicit occasions when they are free for an update.
Finally, consistently ensure that correspondence is straightforward. However anybody can construct a site nowadays, and there are still many valid justifications for hiring dedicated developers.
An expert can do things you can’t and will take care of business faster than you. Re-appropriating this undertaking to another person additionally offers you the chance to focus on more significant things.
What are the best platforms to hire dedicated Node.js developers from India?
Hiring dedicated Node.js developers in India can be a cost-effective and efficient way to leverage this technology for your projects. In this article, we will explore various platforms to find the best Node.js talent in India.
India has earned a reputation for producing highly skilled software developers. When it comes to Node.js development, Indian professionals are no exception. They possess a strong foundation in JavaScript, making it easier for them to adapt to Node.js. Additionally, India offers cost advantages, making it an attractive option for businesses seeking to optimize their development budget.
Freelancing Platforms
Upwork
Upwork is a global freelancing platform that connects businesses with freelance Node.js developers. It offers a wide pool of talent, and you can hire developers based on their skillsets, hourly rates, and reviews from previous clients. Upwork provides a secure payment system and a convenient platform for project management.
Freelancer
Freelancer is another popular platform for hiring Node.js developers on a freelance basis. You can post your project requirements and receive bids from developers interested in your project. Freelancer offers a competitive environment that can help you find developers who meet your specific needs.
Dedicated Development Agencies
Toptal
Toptal is a platform that specializes in connecting businesses with top-tier Node.js developers. They have a rigorous screening process, ensuring you get access to highly skilled professionals. While Toptal’s rates may be higher, the quality of developers they provide is exceptional.
CodigoDelSur
CodigoDelSur is a development agency based in Uruguay, known for its expertise in Node.js development. While not in India, they offer remote development services and have a track record of delivering high-quality solutions. Consider them if you seek a balance between quality and cost-effectiveness.
GraffersID
GraffersID is an Indian-based tech firm specializing in Node.js development. They have a team of experienced Node.js developers who can work on a wide range of projects. GraffersID is known for its commitment to quality and client satisfaction.
Job Portals
LinkedIn is a professional networking platform that also serves as a job portal. You can use its advanced search features to find Node.js developers in India. Additionally, you can view their professional profiles and connect with them directly.
Naukri.com
Naukri.com is one of India’s largest job portals. You can post job listings for Node.js developers and receive applications from qualified candidates. It’s a reliable platform for finding local talent.
Tech Communities and Forums
GitHub
GitHub is a hub for developers worldwide. While it’s not a traditional hiring platform, you can explore Node.js developers’ profiles, review their contributions to open-source projects, and contact them for potential collaborations.
Stack Overflow
Stack Overflow is a community-driven platform where developers ask and answer technical questions. It also has a job board where you can post Node. js-related job listings and connect with developers who are active in the Node.js community.
Tips for successfully outsourcing Node.js development to India
Outsourcing software development has become a popular choice for companies worldwide. One destination that has gained prominence in the outsourcing landscape is India, known for its skilled software developers and competitive pricing. If you’re considering outsourcing Node.js development to India, this article provides you with valuable tips and insights to ensure a successful partnership.
1. Understanding Node.js Development
Before delving into outsourcing, it’s essential to have a good grasp of Node.js. Node.js is an open-source, server-side JavaScript runtime environment used for building fast and scalable network applications. Understanding the basics will help you communicate your project requirements effectively.
2. Why Outsource to India
India has a vast pool of skilled Node.js developers who offer cost-effective solutions. The country’s software industry is well-established, with a reputation for delivering high-quality work. The competitive pricing in India can significantly reduce your development costs.
3. Choosing the Right Outsourcing Partner
Selecting the right outsourcing partner is crucial. Look for companies with a proven track record in Node.js development, positive client reviews, and a portfolio of successful projects.
4. Clear Communication is Key
Effective communication is the cornerstone of successful outsourcing. Establish clear communication channels and ensure both parties are on the same page regarding project goals and expectations.
5. Define Your Project Scope
Clearly define the scope of your project, including features, functionalities, and timelines. This will help prevent scope creep and misunderstandings down the line.
6. Embrace Agile Methodologies
Consider adopting Agile methodologies for project management. Agile allows for flexibility, iterative development, and quick adaptability to changes.
7. Quality Assurance and Testing
Prioritize quality assurance and testing to ensure the final product meets your standards. Discuss testing processes and methodologies with your outsourcing partner.
8. Protecting Your Intellectual Property
Work with legal experts to draft comprehensive contracts that protect your intellectual property rights. Non-disclosure agreements (NDAs) are often essential in outsourcing relationships.
9. Monitor Progress Closely
Regularly monitor the progress of your project. Tools like project management software and regular status meetings can help keep things on track.
10. Budgeting and Cost Control
Establish a clear budget and monitor expenses closely. Effective cost control ensures you stay within budget while receiving quality work.
11. Cultural Sensitivity and Time Zones
Respect cultural differences and be mindful of time zone disparities. Set clear expectations regarding working hours and holidays.
12. Legal Agreements and Contracts
Always have legally binding agreements in place. These contracts should detail project scope, timelines, payment schedules, and dispute resolution mechanisms.
13. Ongoing Support and Maintenance
Discuss post-development support and maintenance with your outsourcing partner. Having a plan in place for updates and bug fixes is essential.
14. Handling Challenges and Conflicts
In any outsourcing relationship, challenges may arise. Address issues promptly and professionally to maintain a healthy partnership.
In the wake of thinking about every one of the means and substeps, did you understand something? You additionally need to have a business justification going this far to draw in programming engineers.
In case you’re searching for instant alternatives, you can likewise go to us – a full-stack programming house that has effectively done this work for you – and re-appropriate improvement to a distant group of qualified, work-fulfilled engineers.
Look at our web improvement administrations and Hire distant software engineers if your advancement needs a lift. Hire Senior Nodejs Developers from GraffersID to guarantee you that your undertaking will be in safe hands.
NodeJS Developers at GraffersID are highly skilled and talented in conveying start-to-finish Nodejs arrangements incorporating them with well-known JavaScript systems and libraries and worker innovations.
Hire Senior NodeJS developers from GraffersID and partake in the top Nodejs advancement arrangements. We adjust our endeavors to your intentions.
We will assist you with improvement, thought approval, business examination, statistical surveying, and contender investigation.
Conclusion
When hiring NodeJS developers, you should know their knowledge concerning the security attacks and vulnerabilities the application can encounter. It will help you secure the code base and source files from the beginning of the development stage. So, the chances of getting an entry into the back-end server or database through the back door will reduce significantly, and your NodeJS application will become safer and more secure.









